GIAC GCED - GIAC Certified Enterprise Defender
You have been tasked with searching for Alternate Data Streams on the following collection of Windows partitions; 2GB FAT16, 6GB FAT32, and 4GB NTFS. How many total Gigabytes and partitions will you need to search?
Which type of attack could be used to obtain IOS router configuration files without a valid user password?
An incident response team investigated a database breach, and determined it was likely the result of an internal user who had a default password in place. The password was changed. A week later, they discover another loss of database records. The database admin provides logs that indicate the attack came from the front-end web interface. Where did the incident response team fail?
When running a Nmap UDP scan, what would the following output indicate?
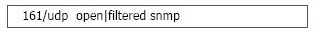
To detect worms and viruses buried deep within a network packet payload, Gigabytes worth of traffic content entering and exiting a network must be checked with which of the following technologies?
Requiring criminal and financial background checks for new employees is an example of what type of security control?



