Huawei H12-725_V4.0 - HCIP-Security V4.0 Exam
Which of the following statements is false about HTTP behavior?
On a WLAN where the WAC has Portal authentication configured, VLAN authorization can be implemented with no additional configuration required. After Portal authentication is complete, the WAC forwards STA traffic based on the authorized VLANs.
IPsec VPN does not support encapsulation of non-IP unicast packets.
Which of the following statements is false about the ATIC system architecture?
Which of the following is not a response action for abnormal file identification?
If data filtering is configured on the firewall but is not correctly referenced in the security policy, the data that should be blocked can still be transmitted normally.
When a user accesses the virtual gateway, the user can access the SSL VPN only after the user terminal passes the host check policy.
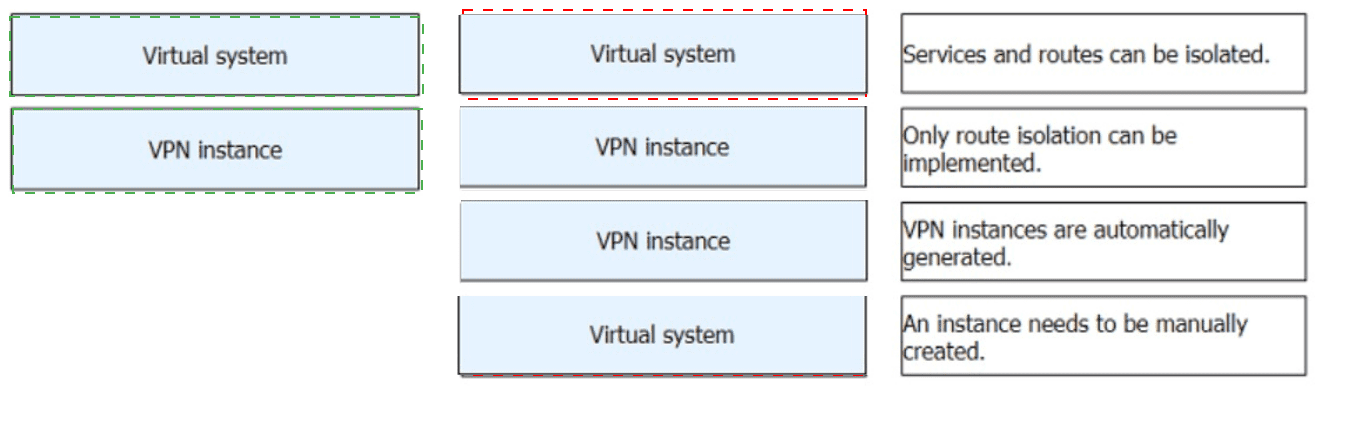
: 51 DRAG DROP
Match the description about virtual systems and VPN instances.