Huawei H12-725_V4.0 - HCIP-Security V4.0 Exam
Which of the following statements is false about web rewriting in web proxy?
*In the data filtering profile on the firewall, keyword group "Keyword" is invoked in the upload direction of HTTP applications, the action is block, and the keyword group is invoked in the security policy. Given this, if the regular expression "b.d" is configured in the keyword group "Keyword,†which of the following texts can be posted by internal employees on the forum?
Which of the following statements is false about health check?
Huawei iMaster NCE-Campus is a web-based centralized management and control system in the CloudCampus Solution. It supports user access management and can function as multiple types of authentication servers. Which of the following servers can iMaster NCE-Campus not be used as?
In the figure, if 802.1X authentication is used for wired users on the network, the network admission device and terminals must be connected through a Layer 2 network.
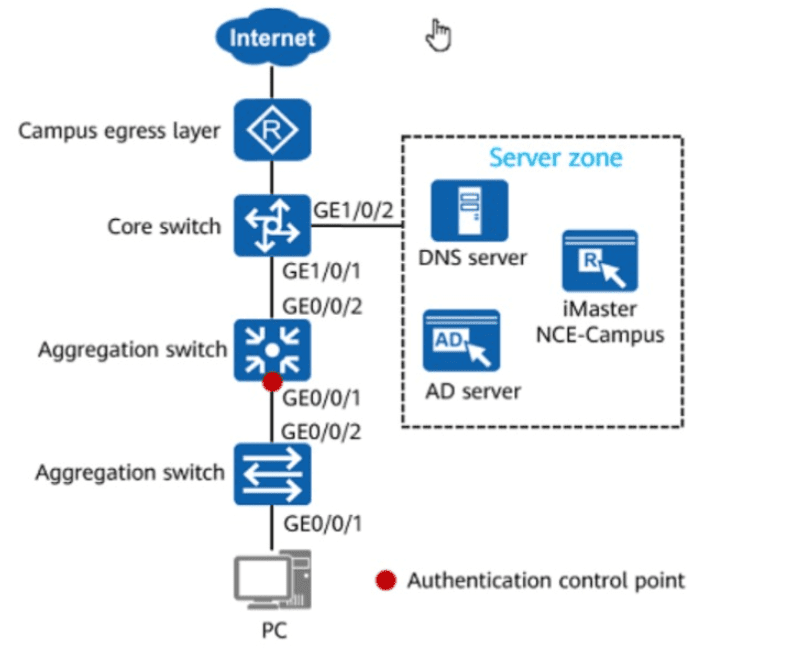
Options:
Which of the following statements is false about Eth-Trunk?(Select All that Apply)
In quota control policies, which of the following can be set for users?(Select All that Apply)
In a Huawei network security environment, which of the following is a key advantage of using HWTACACS over RADIUS for device management authentication?
Options:
The figure shows the defense mechanism of an HTTP flood attack. Which source IP detection technology is displayed in the figure?
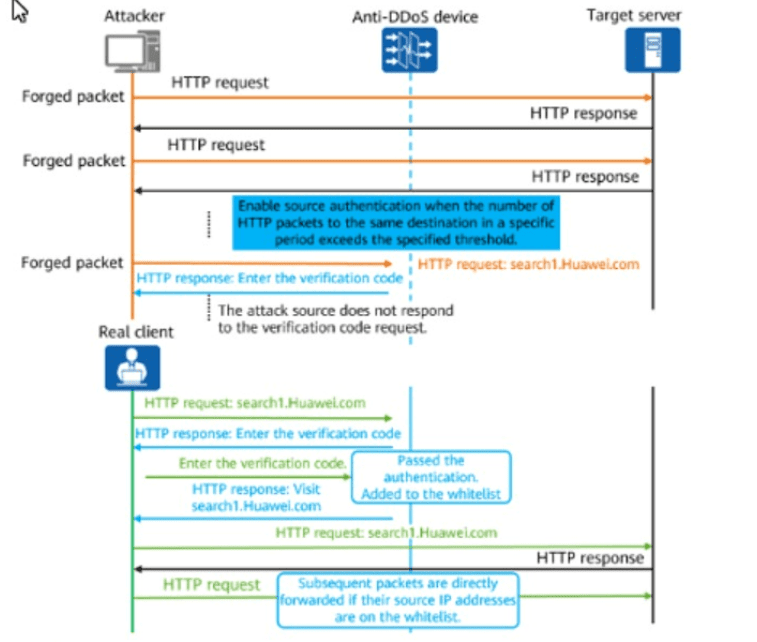
Which of the following items are recorded in the IPS service module logs of a Huawei NGFW?(Select All that Apply)



