HP HPE6-A84 - Aruba Certified Network Security Expert Written Exam
A company has Aruba gateways and wants to start implementing gateway IDS/IPS. The customer has selected Block for the Fail Strategy.
What might you recommend to help minimize unexpected outages caused by using this particular fall strategy?
Refer to the scenario.
A customer is migrating from on-prem AD to Azure AD as its sole domain solution. The customer also manages both wired and wireless devices with Microsoft Endpoint Manager (Intune).
The customer wants to improve security for the network edge. You are helping the customer design a ClearPass deployment for this purpose. Aruba network devices will authenticate wireless and wired clients to an Aruba ClearPass Policy Manager (CPPM) cluster (which uses version 6.10).
The customer has several requirements for authentication. The clients should only pass EAP-TLS authentication if a query to Azure AD shows that they have accounts in Azure AD. To further refine the clients’ privileges, ClearPass also should use information collected by Intune to make access control decisions.
You are planning to use Azure AD as the authentication source in 802.1X services.
What should you make sure that the customer understands is required?
Refer to the scenario.
A hospital has an AOS10 architecture that is managed by Aruba Central. The customer has deployed a pair of Aruba 9000 Series gateways with Security licenses at each clinic. The gateways implement IDS/IPS in IDS mode.
The Security Dashboard shows these several recent events with the same signature, as shown below:
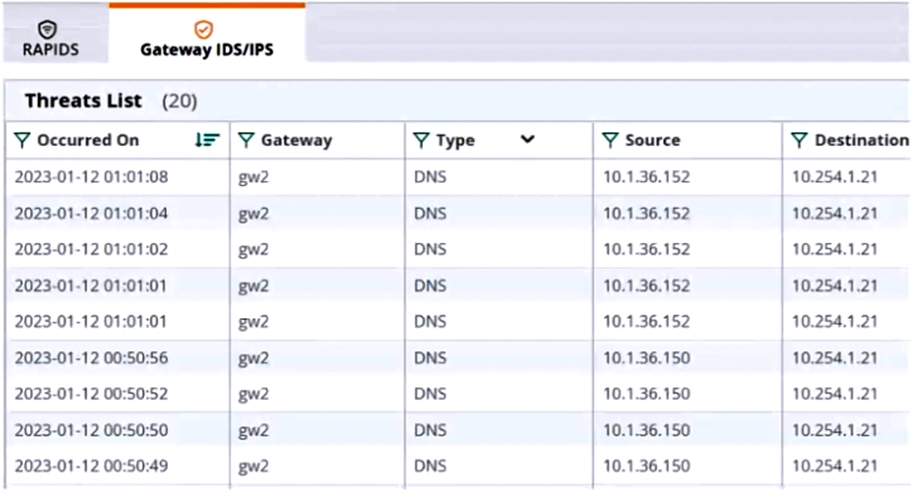
Which step could give you valuable context about the incident?
Refer to the exhibit.
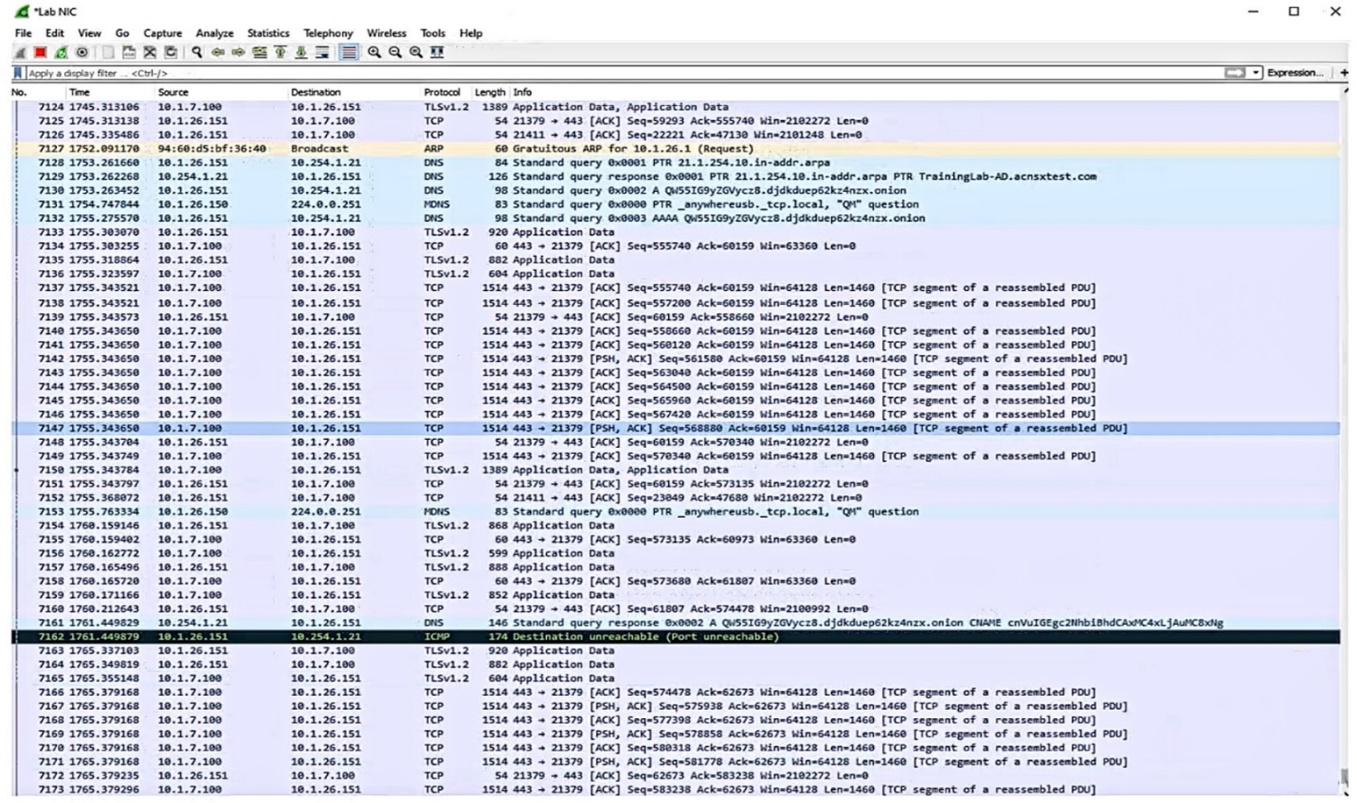
Which IP address should you record as a possibly compromised client?
Refer to the scenario.
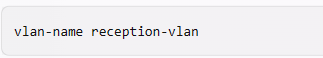
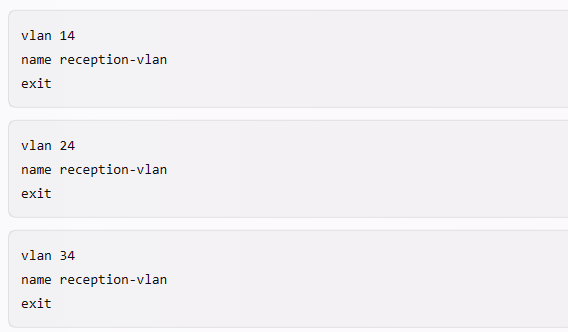
This customer is enforcing 802.1X on AOS-CX switches to Aruba ClearPass Policy Manager (CPPM). The customer wants switches to download role settings from CPPM. The “reception-domain†role must have these settings:
— Assigns clients to VLAN 14 on switch 1, VLAN 24 on switch 2, and so on.
— Filters client traffic as follows:
— Clients are permitted full access to 10.1.5.0/24 and the Internet
— Clients are denied access to 10.1.0.0/16
The switch topology is shown here:
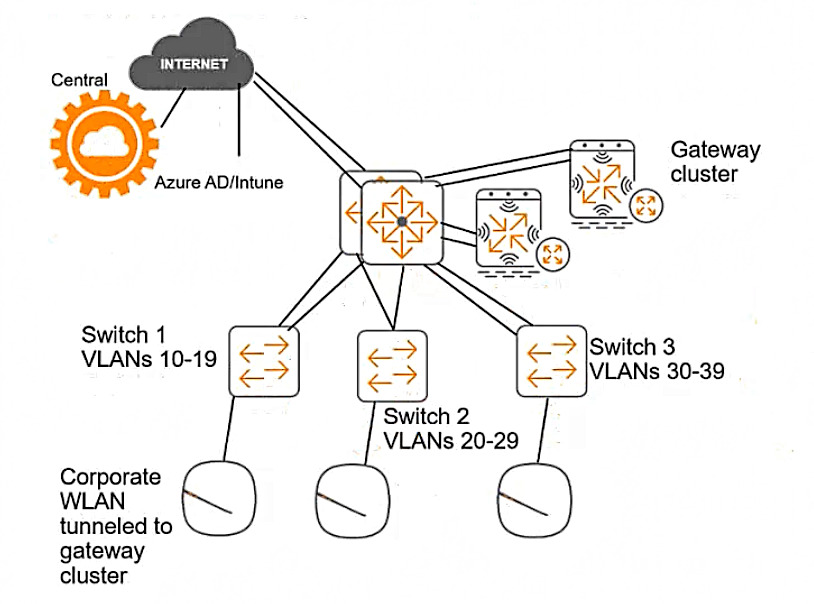
How should you configure the VLAN setting for the reception role?
Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement 802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba gateway cluster. The gateway cluster should assign these clients to the “eth-internet" role. The gateway should also handle assigning clients to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below:
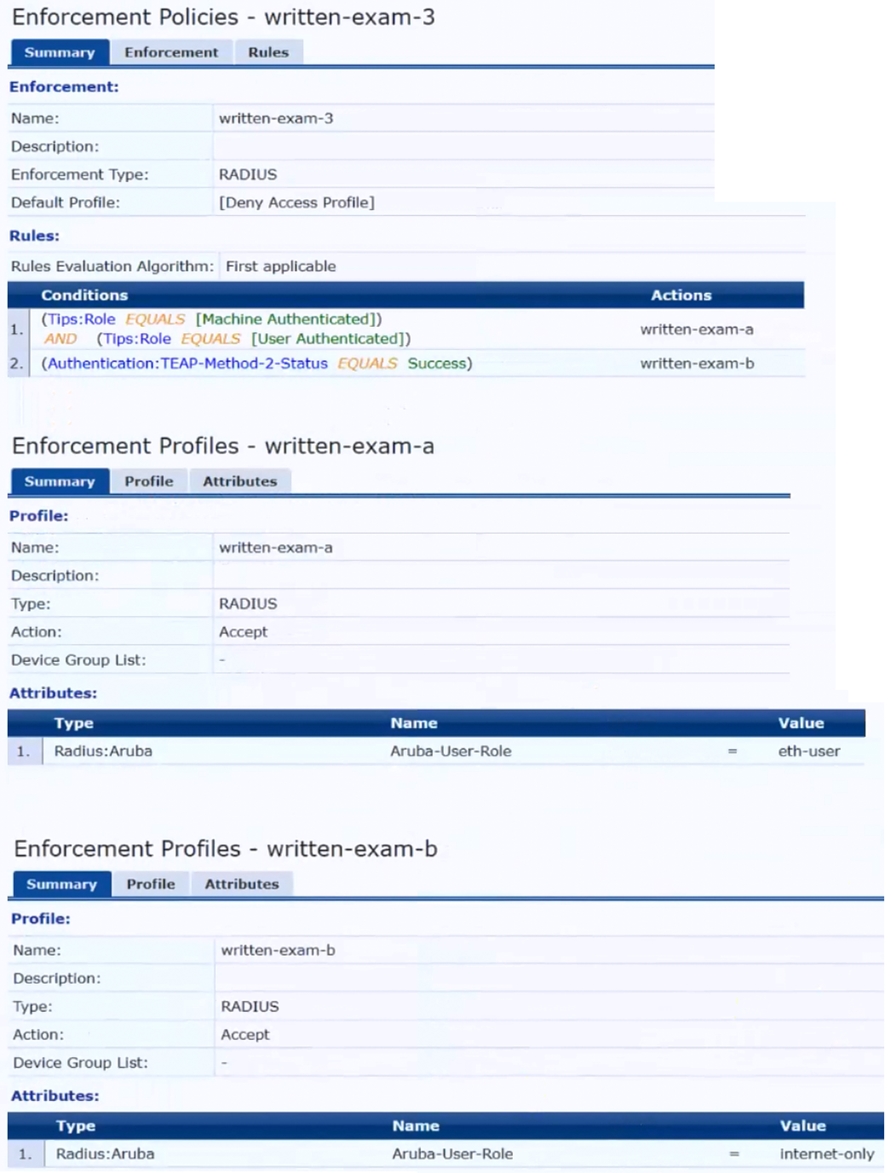
The gateway cluster has two gateways with these IP addresses:
• Gateway 1
o VLAN 4085 (system IP) = 10.20.4.21
o VLAN 20 (users) = 10.20.20.1
o VLAN 4094 (WAN) = 198.51.100.14
• Gateway 2
o VLAN 4085 (system IP) = 10.20.4.22
o VLAN 20 (users) = 10.20.20.2
o VLAN 4094 (WAN) = 198.51.100.12
• VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster. If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
What is one change that you should make to the solution?
The customer needs a way for users to enroll new wired clients in Intune. The clients should have limited access that only lets them enroll and receive certificates. You plan to set up these rights in an AOS-CX role named “provision.â€
The customer’s security team dictates that you must limit these clients’ Internet access to only the necessary sites. Your switch software supports IPv4 and IPv6 addresses for the rules applied in the “provision†role.
What should you recommend?
A customer has an AOS 10 architecture, which includes Aruba APs. Admins have recently enabled WIDS at the high level. They also enabled alerts and email notifications for several events, as shown in the exhibit.
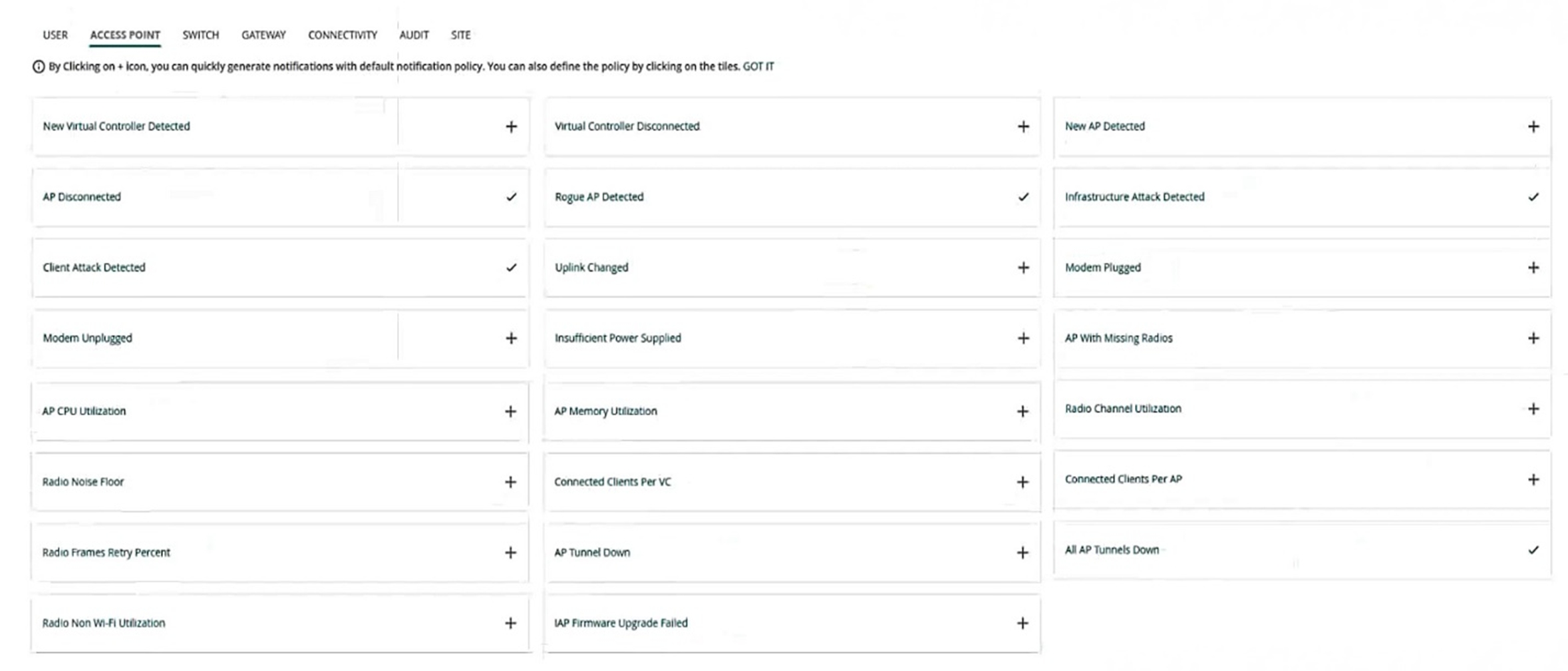
Admins are complaining that they are getting so many emails that they have to ignore them, so they are going to turn off all notifications.
What is one step you could recommend trying first?