HP HPE7-A02 - Aruba Certified Network Security Professional Exam
A company has AOS-CX switches and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company wants switches to implement 802.1X authentication to CPPM and download user roles. What is one task that you must complete on CPPM to support this use case?
As part of setting up an HPE Aruba Networking ClearPass Onboard solution for wireless clients, you created Network Settings, a Configuration Profile, and a Provisioning Settings object in ClearPass Onboard. You also ran the ClearPass Onboard Service Only Template on ClearPass Policy Manager (CPPM).
You now need to ensure that only domain users are authenticated and allowed to log into the ClearPass Onboard portal.
Which component should you edit?
A company is implementing HPE Aruba Networking Wireless IDS/IPS (WIDS/WIPS) on its AOS-10 APs, which are managed in HPE Aruba Networking Central.
What is one requirement for enabling detection of rogue APs?
HPE Aruba Networking Central displays an alert about an Infrastructure Attack that was detected. You go to the Security > RAPIDS events and see that the attack
was "Detect adhoc using Valid SSID."
What is one possible next step?
What is one use case for implementing user-based tunneling (UBT) on AOS-CX switches?
A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as a TACACS+ server to authenticate managers on its AOS-CX switches. The
company wants CPPM to control which commands managers are allowed to enter. You see there is no field to enter these commands in ClearPass.
How do you start configuring the command list on CPPM?
Which statement describes Zero Trust Security?
You are establishing a cluster of HPE Aruba Networking ClearPass servers. (Assume that they are running version 6.9.).
For which type of certificate it is recommended to install a CA-signed certificate on the Subscriber before it joins the cluster?
What is a use case for the HPE Aruba Networking ClearPass OnGuard dissolvable agent?
Refer to the Exhibit:
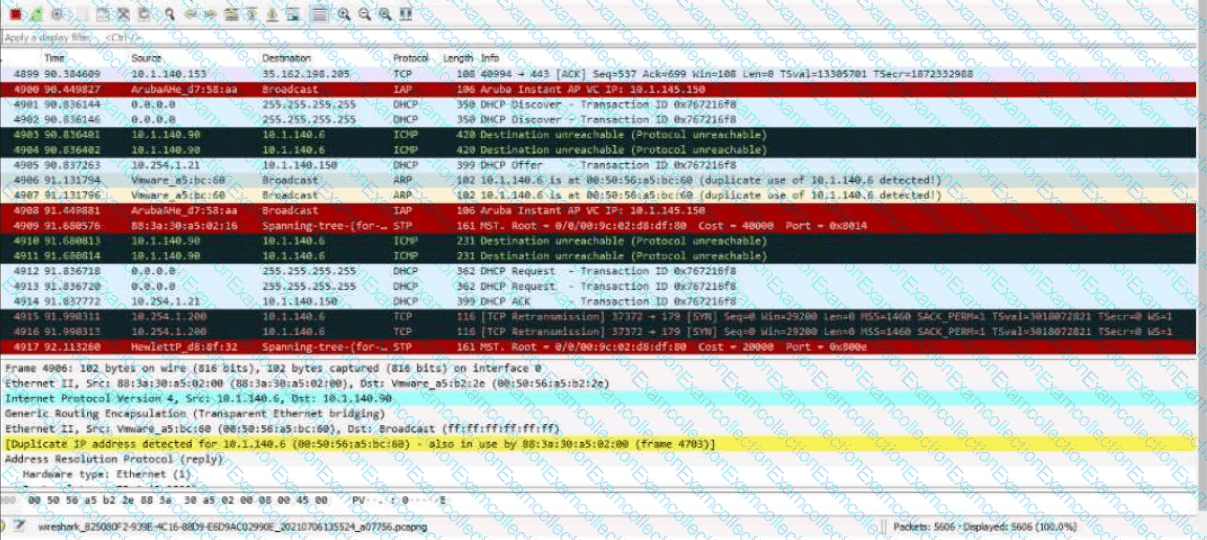
These packets have been captured from VLAN 10. which supports clients that receive their IP addresses with DHCP.
What can you interpret from the packets that you see here?
These packets have been captured from VLAN 10, which supports clients that receive their IP addresses with DHCP. What can you interpret from the packets that you see here?



