HP HPE7-A02 - Aruba Certified Network Security Professional Exam
A company wants to turn on Wireless IDS/IPS infrastructure and client detection at the high level on HPE Aruba Networking APs. The company does not want to
enable any prevention settings.
What should you explain about HPE Aruba Networking recommendations?
A company wants HPE Aruba Networking ClearPass Policy Manager (CPPM) to respond to Syslog messages from its Palo Alto Next Generation Firewall (NGFW)
by quarantining clients involved in security incidents.
Which step must you complete to enable CPPM to process the Syslogs properly?
You need to set up HPE Aruba Networking ClearPass Policy Manager (CPPM) to provide certificate-based authentication of 802.1X supplicants.
How should you upload the root CA certificate for the supplicants' certificates?
A company has HPE Aruba Networking APs, which authenticate users to HPE Aruba Networking ClearPass Policy Manager (CPPM).
What does HPE Aruba Networking recommend as the preferred method for assigning clients to a role on the AOS firewall?
Refer to Exhibit:
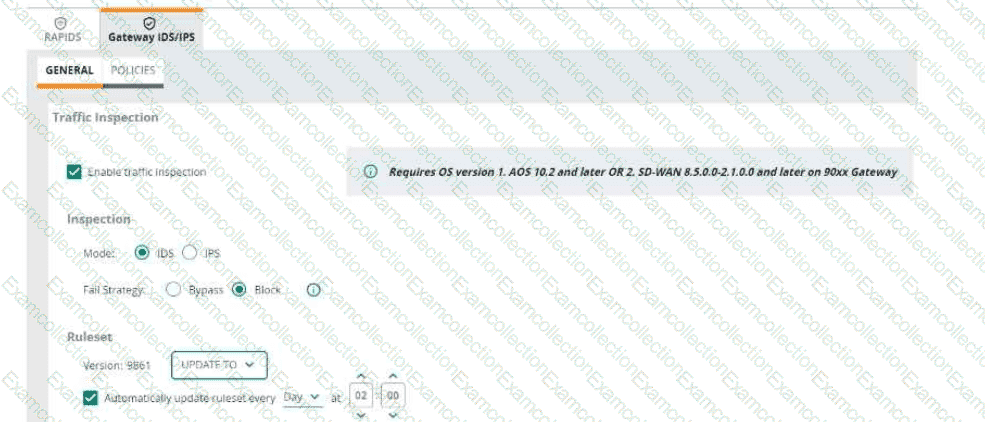
An HPE Aruba Networking 9x00 gateway is part of an HPE Aruba Networking Central group that has the settings shown in the exhibit. What would cause the gateway to drop traffic as part of its IDPS settings?
You need to create a rule in an HPE Aruba Networking ClearPass Policy Manager (CPPM) role mapping policy that references a ClearPass Device Insight Tag.
Which Type (namespace) should you specify for the rule?
You want to examine the applications that a device is using and look for any changes in application usage over several different ranges. In which HPE Aruba Networking solution can you view this information in an easy-to-view format?
You are configuring the HPE Aruba Networking ClearPass Device Insight Integration settings on ClearPass Policy Manager (CPPM). For which use case should you set the 'Tag Updates Action" to "apply for all tag updates"?
HPE Aruba Networking Central displays a Gateway Threat Count alert in the alert list. How can you gather more information about what caused the alert to trigger?
A company has HPE Aruba Networking APs managed by HPE Aruba Networking Central. You have set up a WLAN to enforce WPA3 with 802.1X authentication.
What happens if the client fails authentication?



