HP HPE7-A02 - Aruba Certified Network Security Professional Exam
A company wants you to integrate HPE Aruba Networking ClearPass Policy Manager (CPPM) with HPE Aruba Networking ClearPass Device Insight (CPDI).
What is one aspect of the integration that you should explain?
You are proposing HPE Aruba Networking ZTNA to an organization that currently uses a third-party, IPsec-based client-to-site VPN.
What is one advantage of ZTNA that you should emphasize?
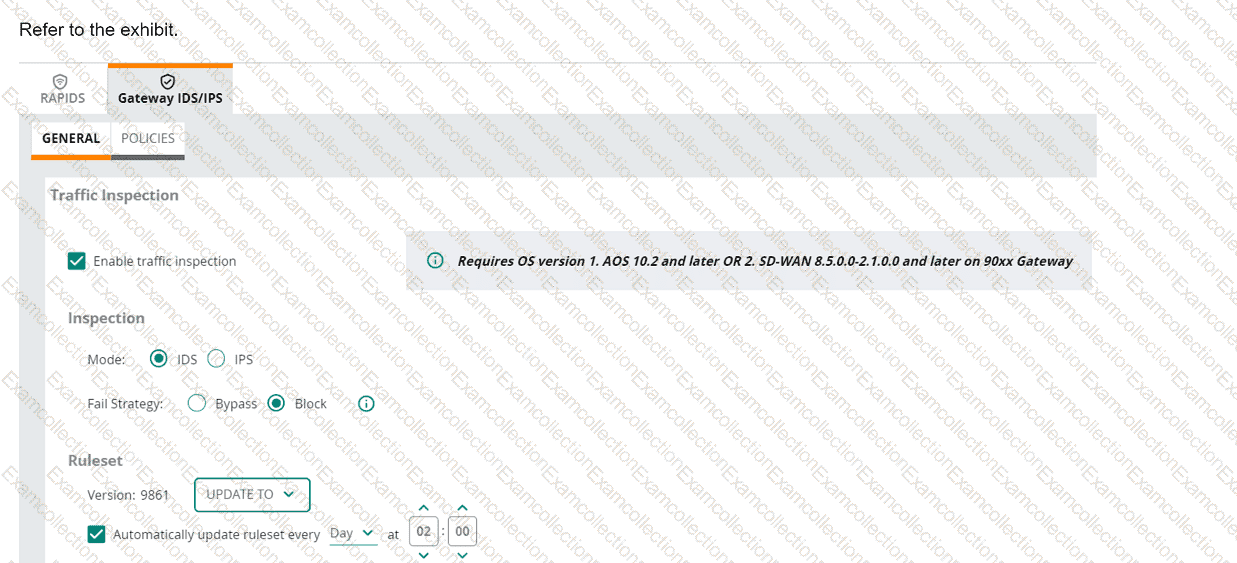
(Note that the HPE Aruba Networking Central interface shown here might look slightly different from what you see in your HPE Aruba Networking Central
interface as versions change; however, similar concepts continue to apply.)
An HPE Aruba Networking 9x00 gateway is part of an HPE Aruba Networking Central group that has the settings shown in the exhibit. What would cause the
gateway to drop traffic as part of its IDPS settings?
You are using OpenSSL to obtain a certificate signed by a Certification Authority (CA). You have entered this command:
openssl req -new -out file1.pem -newkey rsa:3072 -keyout file2.pem
Enter PEM pass phrase: **********
Verifying - Enter PEM pass phrase: **********
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:California
Locality Name (eg, city) []:Sunnyvale
Organization Name (eg, company) [Internet Widgits Pty Ltd]:example.com
Organizational Unit Name (eg, section) []:Infrastructure
Common Name (e.g. server FQDN or YOUR name) []:radius.example.com
What is one guideline for continuing to obtain a certificate?
A company wants to use the HPE Aruba Networking ClearPass OnGuard agent to assign posture to clients.
How do you define the conditions by which a client receives a particular posture?
A company uses both HPE Aruba Networking ClearPass Policy Manager (CPPM) and HPE Aruba Networking ClearPass Device Insight (CPDI).
What is one way integrating the two solutions can help the company implement Zero Trust Security?
An AOS-CX switch has this admin user account configured on it:
netadmin in the operators group.
You have configured these commands on an AOS-CX switch:
tacacs-server host cp.example.com key plaintext &12xl,powmay7855
aaa authentication login ssh group tacacs local
aaa authentication allow-fail-through
A user accesses the switch with SSH and logs in as netadmin with the correct password. When the switch sends a TACACS+ request to the ClearPass server at cp.example.com, the server does not send a response. Authentication times out.
What happens?
Refer to Exhibit.
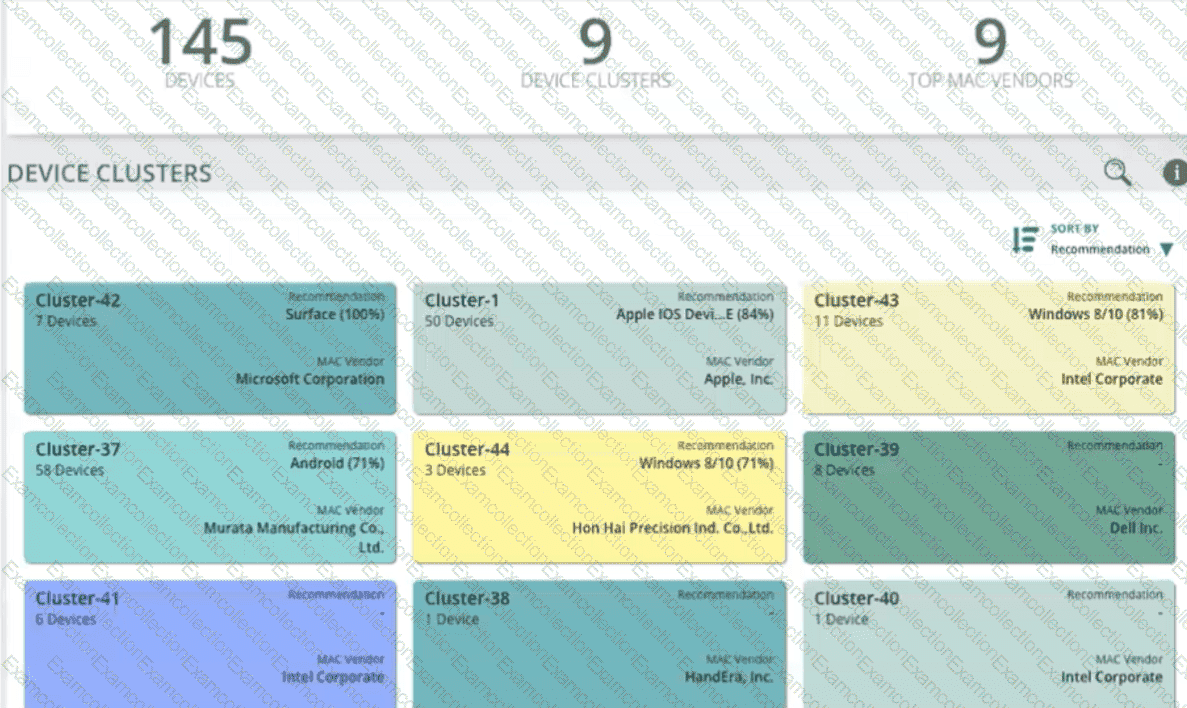
A company is using HPE Aruba Networking ClearPass Device Insight (CPDI) (the standalone application). In the CPDI interface, you go to the Generic Devices
page and see the view shown in the exhibit.
What correctly describes what you see?
A company has several use cases for using its AOS-CX switches' HPE Aruba Networking Network Analytics Engine (NAE).
What is one guideline to keep in mind as you plan?
You have installed an HPE Aruba Networking Network Analytic Engine (NAE) script on an AOS-CX switch to monitor a particular function.
Which additional step must you complete to start the monitoring?



