Juniper JN0-232 - Security, Associate (JNCIA-SEC)
You want to use Avira Antivirus.
Which two actions should you perform to satisfy this requirement? (Choose two.)
You want to show the effectiveness of your SRX Series Firewall content filter.
Which operational mode command would you use in this scenario?
You are asked to create a security policy that controls traffic allowed to pass between the Internet and private security zones. You must ensure that this policy is evaluated before all other policy types on your SRX Series device.
In this scenario, which type of security policy should you create?
Which two statements about global security policies are correct? (Choose two.)
What is transit traffic in the Junos OS?
What happens if no match is found in both zone-based and global security policies?
Which two criteria would be used for matching in security policies? (Choose two.)
Click the Exhibit button.
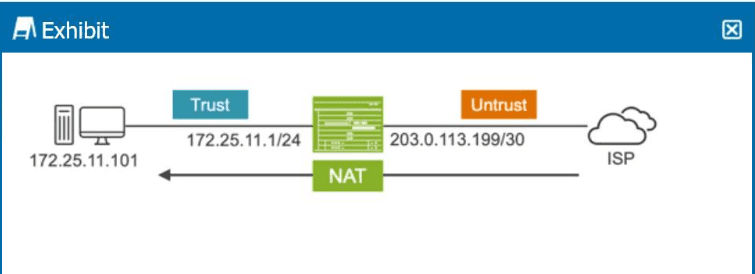
You must ensure that sessions can only be established from the external device.
Referring to the exhibit, which type of NAT is being performed?
Click the Exhibit button.
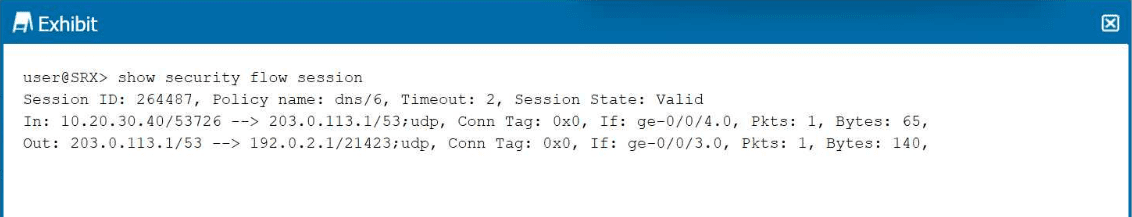
Referring to the exhibit, which two statements are correct about the traffic flow shown in the exhibit? (Choose two.)



