Juniper JN0-232 - Security, Associate (JNCIA-SEC)
You are modifying the NAT rule order and you notice that a new NAT rule has been added to the bottom of the list.
In this situation, which command would you use to reorder NAT rules?
What are two ways that an SRX Series device identifies content? (Choose two.)
You want to enable NextGen Web Filtering in SRX Series devices.
In this scenario, which two actions will accomplish this task? (Choose two.)
You have created a series of security policies permitting access to a variety of services. You now want to create a policy that blocks access to all other services for all user groups.
What should you create in this scenario?
Click the Exhibit button.
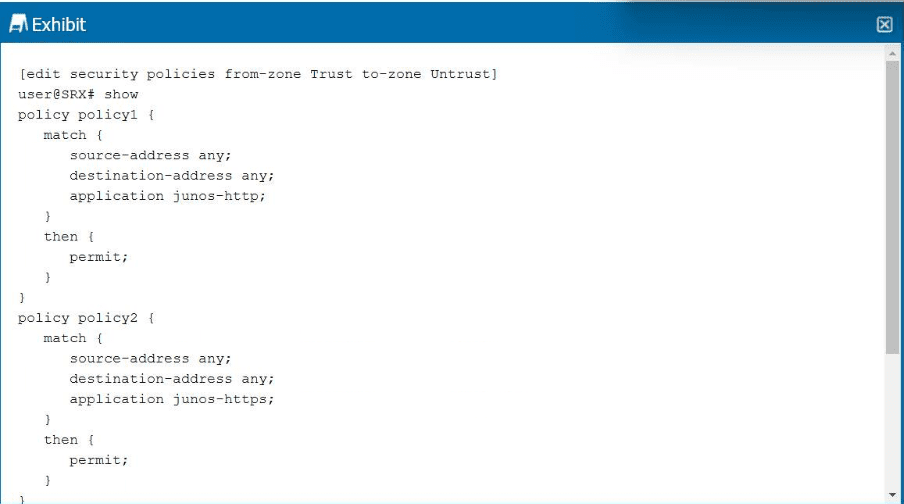

Referring to the exhibit, which statement is correct?
A new packet arrives on an interface on your SRX Series Firewall that is assigned to the trust security zone.
In this scenario, how does the SRX Series Firewall determine the egress security zone?
In which order does Junos OS process the various forms of NAT?
Which statement is correct about capturing transit packets on an SRX Series Firewall?
Click the Exhibit button.
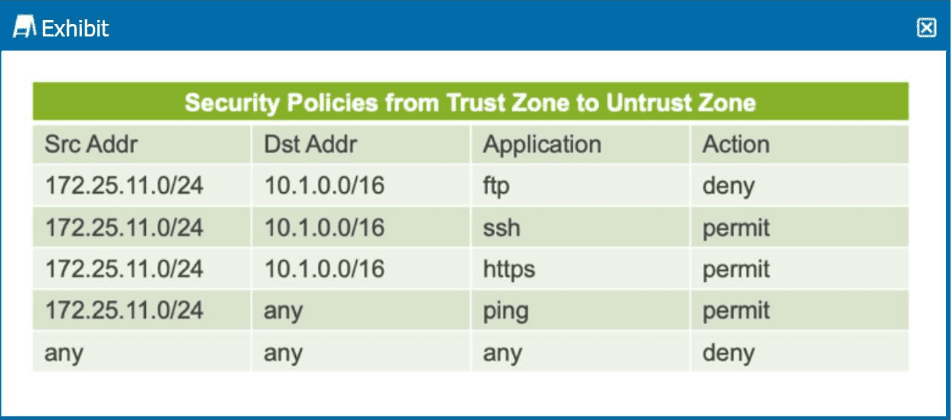
The exhibit shows a table representing security policies from the trust zone to the untrust zone.
In this scenario, which two statements are correct? (Choose two.)
What must also be enabled when using source NAT if the address pool is in the same subnet as the interface?



