Salesforce MuleSoft-Platform-Architect-I - Salesforce Certified MuleSoft Platform Architect (Mule-Arch-201)
Total 152 questions
A large lending company has developed an API to unlock data from a database server and web server. The API has been deployed to Anypoint Virtual Private Cloud
(VPC) on CloudHub 1.0.
The database server and web server are in the customer's secure network and are not accessible through the public internet. The database server is in the customer's AWS
VPC, whereas the web server is in the customer's on-premises corporate data center.
How can access be enabled for the API to connect with the database server and the web server?
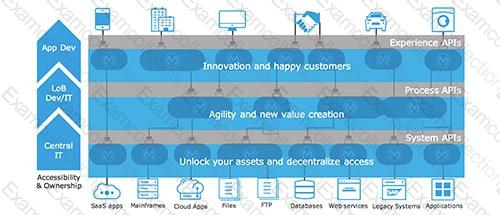
Select the correct Owner-Layer combinations from below options
An organization has built an application network following the API-led connectivity approach recommended by MuleSoft. To protect the application network against
attacks from malicious external API clients, the organization plans to apply JSON Threat Protection policies.
To which API-led connectivity layer should the JSON Threat Protection policies most commonly be applied?
An Anypoint Platform organization has been configured with an external identity provider (IdP) for identity management and client management. What credentials or token must be provided to Anypoint CLI to execute commands against the Anypoint Platform APIs?
A circuit breaker strategy is planned in order to meet the goal of improved response time and demand on a downstream API.
* Circuit Open: More than 10 errors per minute for three minutes
* Circuit Half-Open: One error per minute
* Circuit Closed: Less than one error per minute for five minutes
Out of several proposals from the engineering team, which option will meet this goal?