Fortinet NSE4_FGT_AD-7.6 - Fortinet NSE 4 - FortiOS 7.6 Administrator
Refer to the exhibits.
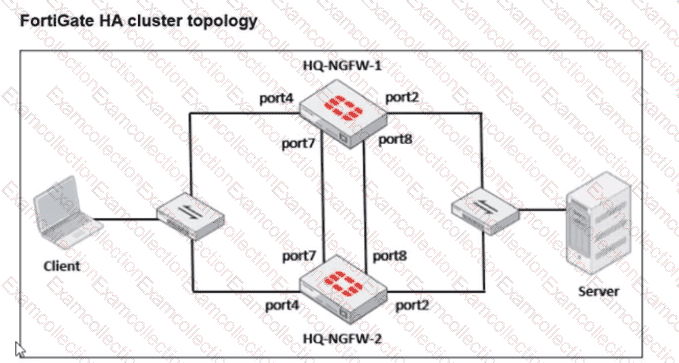
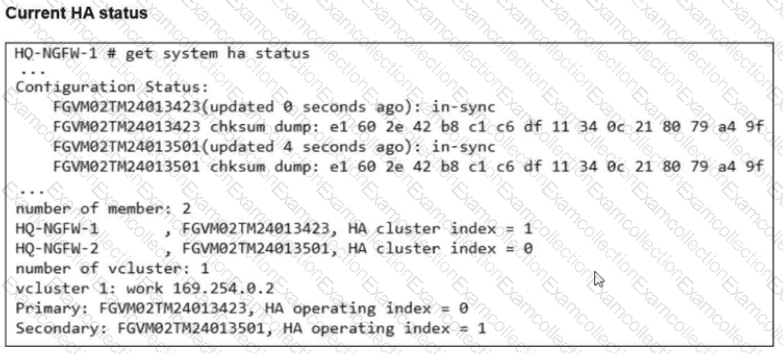
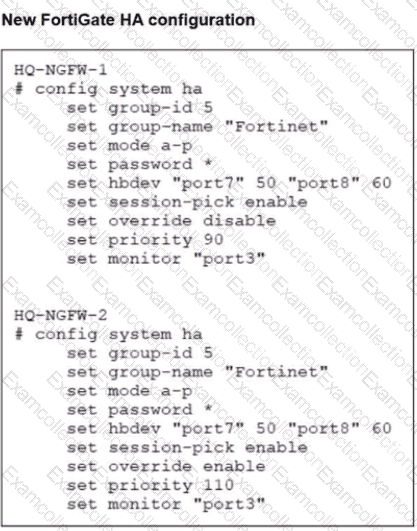
Based on the current HA status, an administrator updates the override and priority parameters on HQ-NGFW-1 and HQ-NGFW-2 as shown in the exhibits.
What would be the expected outcome in the HA cluster?
Refer to the exhibit.
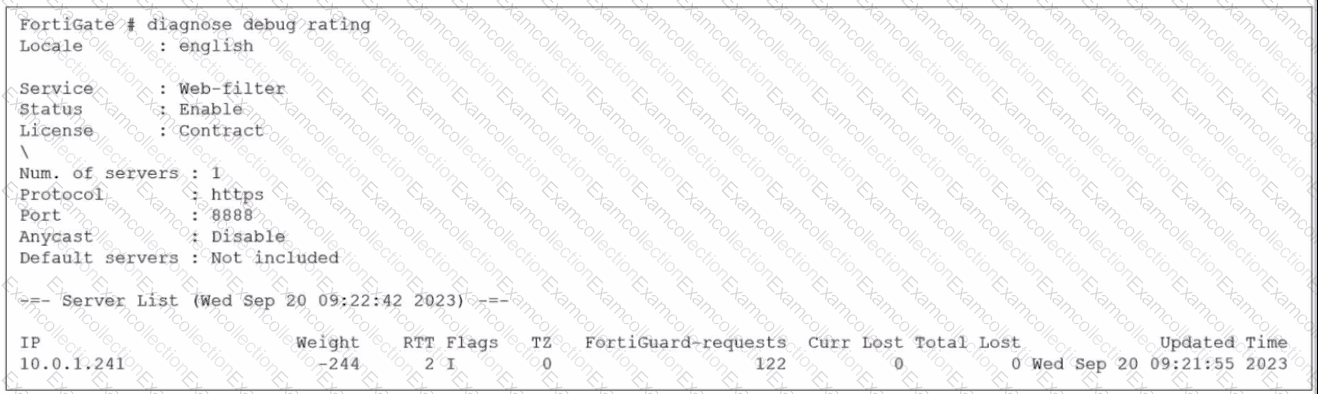
Which two statements about the FortiGuard connection are true? (Choose two.)
Which two statements describe characteristics of automation stitches? (Choose two answers)
Refer to the exhibit.
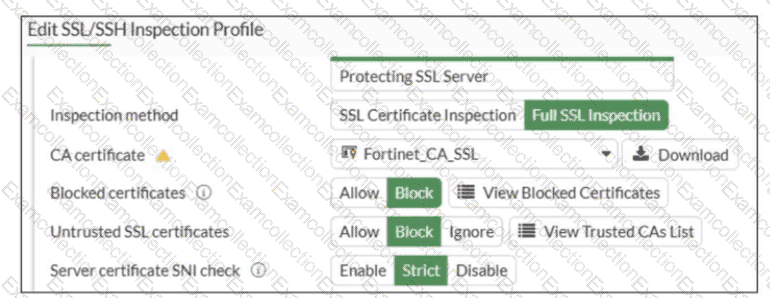
What would be the impact of these settings on the Server certificate SNI check configuration on FortiGate?
How does FortiExtender connect to FortiSASE in a site-based, remote internet access method?
Refer to the exhibit.
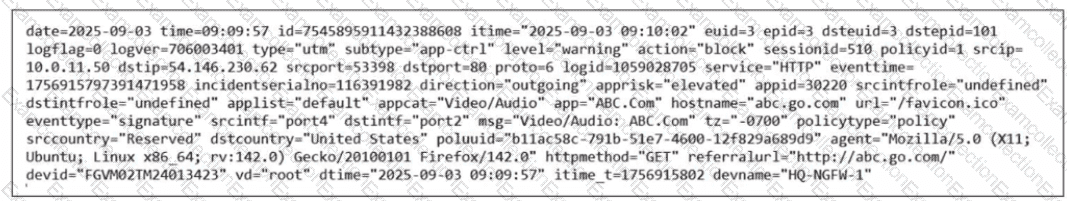
Which two ways can you view the log messages shown in the exhibit? (Choose two.)
Refer to the exhibits.
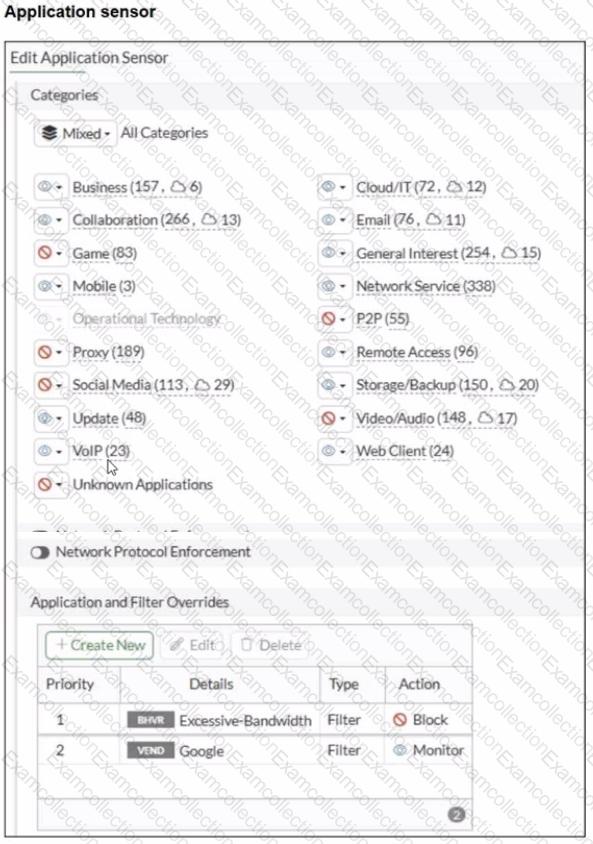
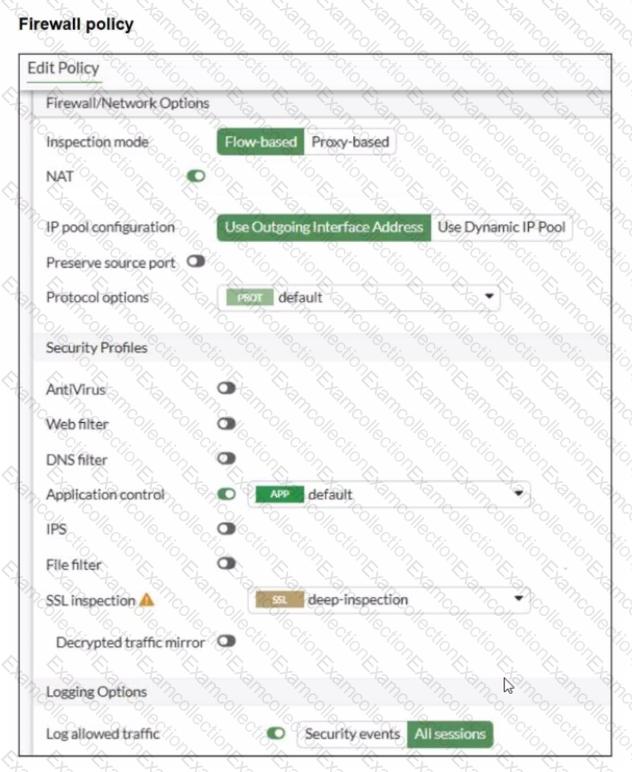
You have implemented the application sensor and the corresponding firewall policy as shown in the exhibits.
Which two factors can you observe from these configurations? (Choose two.)
FortiGate is integrated with FortiAnalyzer and FortiManager.
When creating a firewall policy, which attribute must an administrator include to enhance functionality and enable log recording on FortiAnalyzer and FortiManager?



