Fortinet NSE4_FGT_AD-7.6 - Fortinet NSE 4 - FortiOS 7.6 Administrator
Refer to the exhibits.
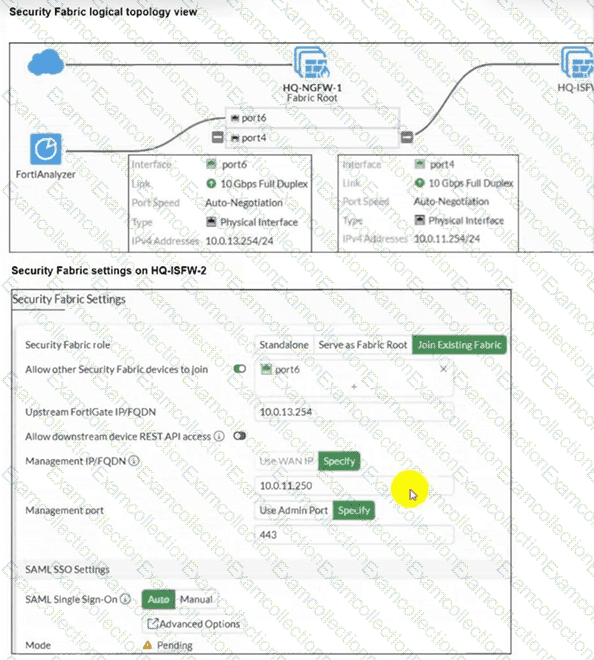
An administrator wants to add HQ-ISFW-2 in the Security Fabric. HQ-ISFW-2 is in the same subnet as HQ-ISFW. After configuring the Security Fabric settings on HQ-ISFW-2, the status stays Pending. What can be the two possible reasons? (Choose two answers)
Refer to the exhibit.
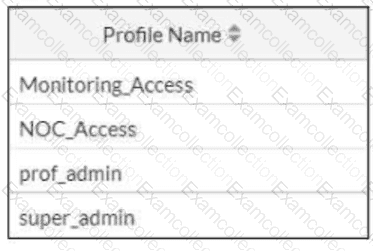
The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that their GUI sessions do not disconnect too early during inactivity. What must the administrator configure to answer this specific request from the NOC team? (Choose one answer)
You have configured the below commands on a FortiGate.
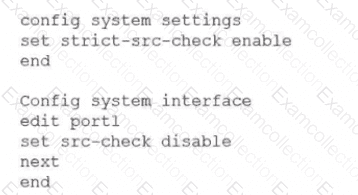
What would be the impact of this configuration on FortiGate?
Refer to the exhibit.
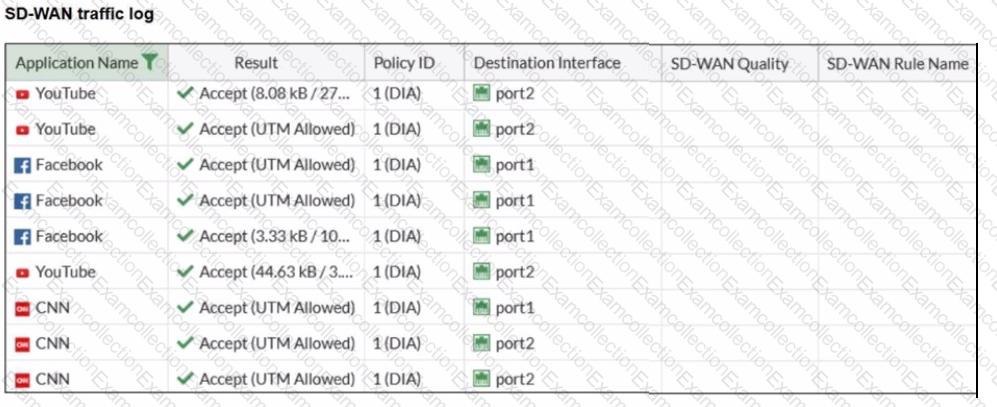
The administrator configured SD-WAN rules and set the FortiGate traffic log page to display SD-WAN-specific columns: SD-WAN Quality and SD-WAN Rule Name
FortiGate allows the traffic according to policy ID 1 placed at the top. This is the policy that allows SD-WAN traffic. Despite these settings, the traffic logs do not show the name of the SD-WAN rule used to steer those traffic flows
What could be the reason?
What are two features of FortiGate FSSO agentless polling mode? (Choose two.)
You have configured an application control profile, set peer-to-peer traffic to Block under the Categories tab. and applied it to the firewall policy. However, your peer-to-peer traffic on known ports is passing through the FortiGate without being blocked.
What FortiGate settings should you check to resolve this issue?
Refer to the exhibits.

The system performance output and default configuration of high memory usage thresholds on a FortiGate device are shown.
Based on the system performance output, what are the two possible outcomes? (Choose two.)
Which three statements explain a flow-based antivirus profile? (Choose three answers)
Refer to the exhibit.

Based on this partial configuration, what are the two possible outcomes when FortiGate enters conserve mode? (Choose two.)
Refer to the exhibits.
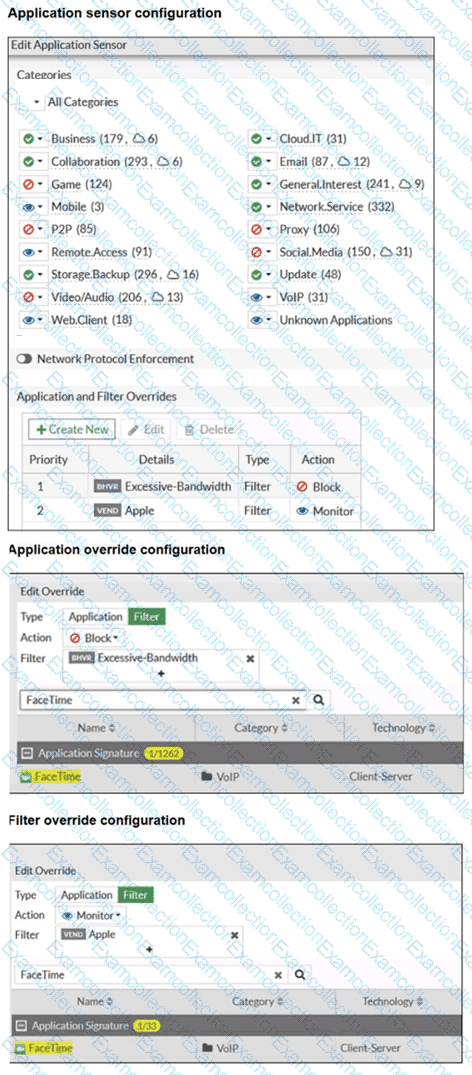
The exhibits show the application sensor configuration and the Excessive-Bandwidth and Apple filter details. Based on the configuration, what will happen to Apple FaceTime if there are only a few calls originating or incoming? (Choose one answer)



