Fortinet NSE6_SDW_AD-7.6 - Fortinet NSE 6 - SD-WAN 7.6 Enterprise Administrator
(In the context of SD-WAN, the terms underlay and overlay are commonly used to categorize links.
Which two statements about underlay and overlay links are correct? Choose two answers.)
You have configured the performance SLA with the probe mode as Prefer Passive.
What are two observable impacts of this configuration? (Choose two.)
(You want FortiGate to use SD-WAN rules to steer ping local-out traffic.
Which two constraints should you consider? Choose two answers.)
Refer to the exhibit.
Which statement best describe the role of the ADVPN device in handling traffic?
Refer to the exhibits.
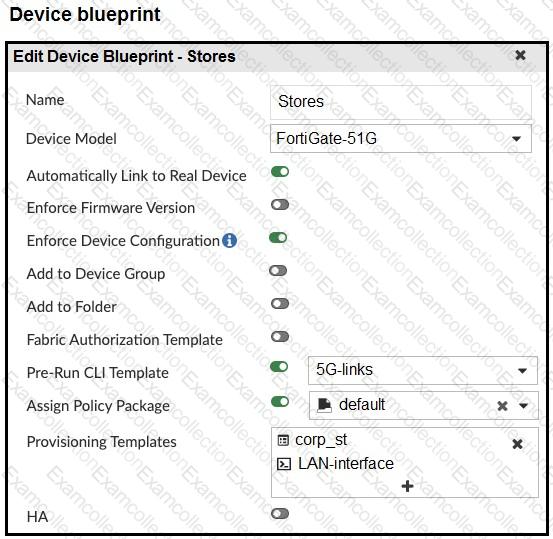
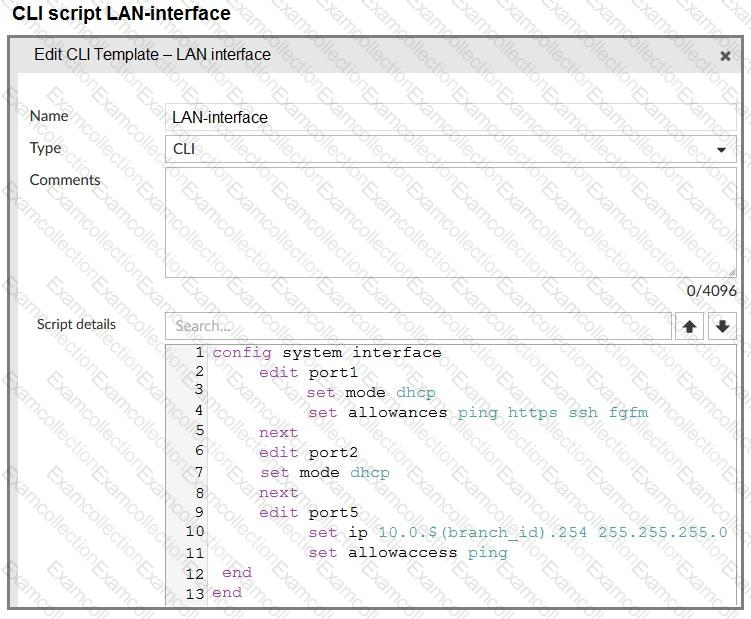
The administrator configured a device blueprint and CLI scripts as shown in the exhibits, to prepare for onboarding FortiGate devices in the company’s stores. Later, a technician prepares a FortiGate 51G with a basic configuration and connects it to the network. The basic configuration contains the port1 configuration and the minimal configuration required to allow the device to connect to FortiManager.
After the device first connects to FortiManager, FortiManager updates the device configuration.
Based on the exhibits, which actions does FortiManager perform?
An SD-WAN member is no longer used to steer SD-WAN traffic. The administrator updated the SD-WAN configuration and deleted the unused member. After the configuration update, users report that some destinations are unreachable. You confirm that the affected flow does not match an SD-WAN rule.
What could be a possible cause of the traffic interruption?
Your FortiGate is in production. To optimize WAN link use and improve redundancy, you enable and configure SD-WAN.
What must you do as part of this configuration update process?
Refer to the exhibit.
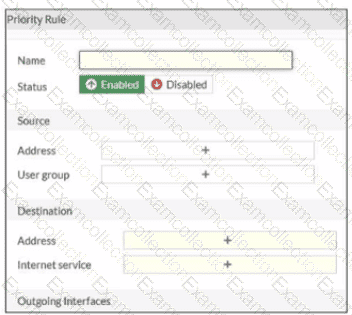
An administrator configures SD-WAN rules for a DIA setup using the FortiGate GUI. The page to configure the source and destination part of the rule looks as shown in the exhibit. The GUI page shows no option to configure an application as the destination of the SD-WAN rule Why?
Refer to the exhibits.
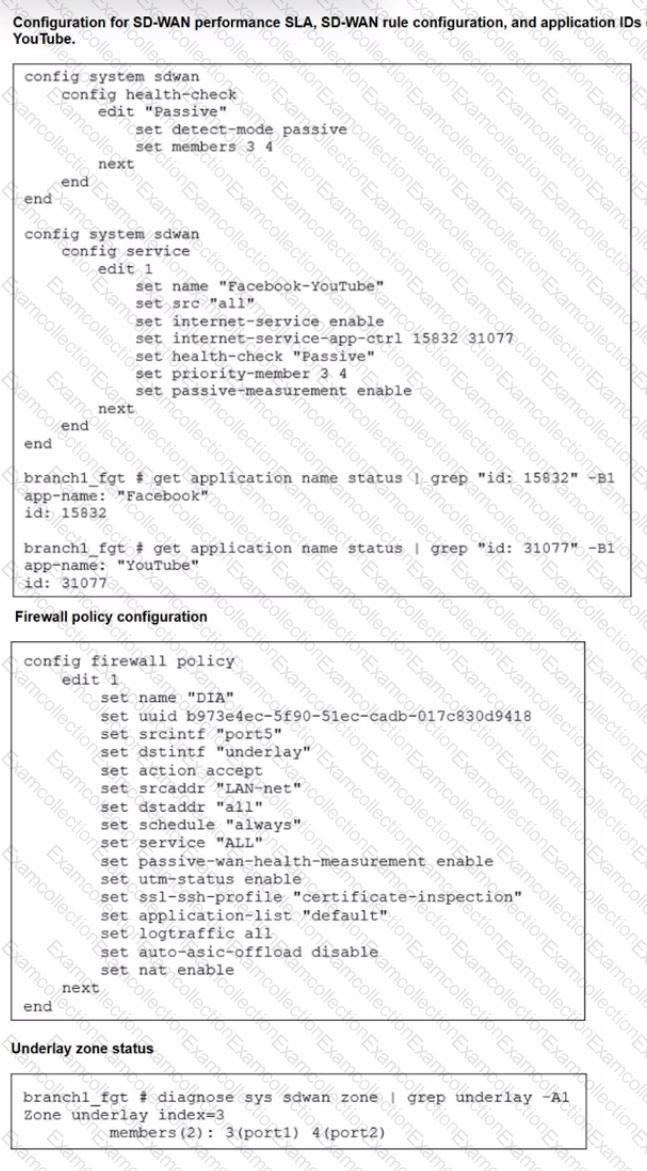
The exhibits show the configuration for SD-WAN performance. SD-WAN rule, the application IDs of Facebook and YouTube along with the firewall policy configuration and the underlay zone status.
Which two statements are true about the health and performance of SD-WAN members 3 and 4? (Choose two.)
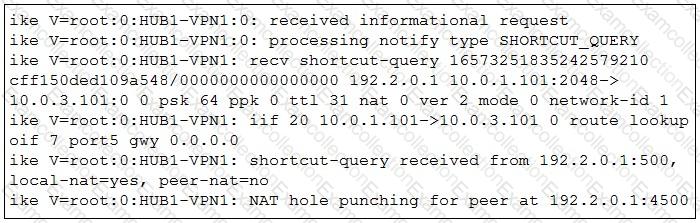
Refer to the exhibit that shows a diagnose output on FortiGate.
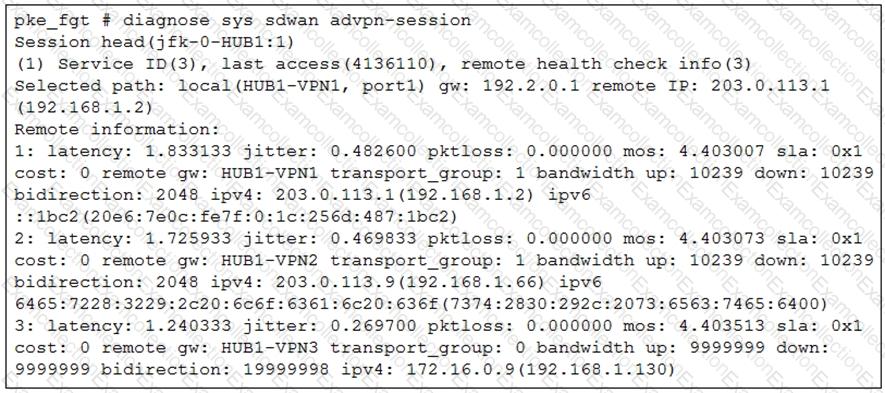
Based on the output shown in the exhibit, what can you say about the device role and how it handles health checks?



