Fortinet NSE6_SDW_AD-7.6 - Fortinet NSE 6 - SD-WAN 7.6 Enterprise Administrator
An administrator is configuring SD-WAN to load balance their network traffic. Which two things should they consider when setting up SD-WAN? (Choose two.)
(Which two features must you configure before FortiGate can steer traffic according to SD-WAN rules? Choose two answers.)
As an IT manager for a healthcare company, you want to delegate the installation and management of your SD-WAN deployment to a managed security service provider (MSSP). Each site must maintain direct internet access and ensure that it is secure. You expected significant traffic flow between the sites and want to delegate as much of the network administration and management as possible to the MSSP.
Which two MSSP deployment blueprints best address the customer’s requirements? (Choose two.)
(Refer to the exhibits.
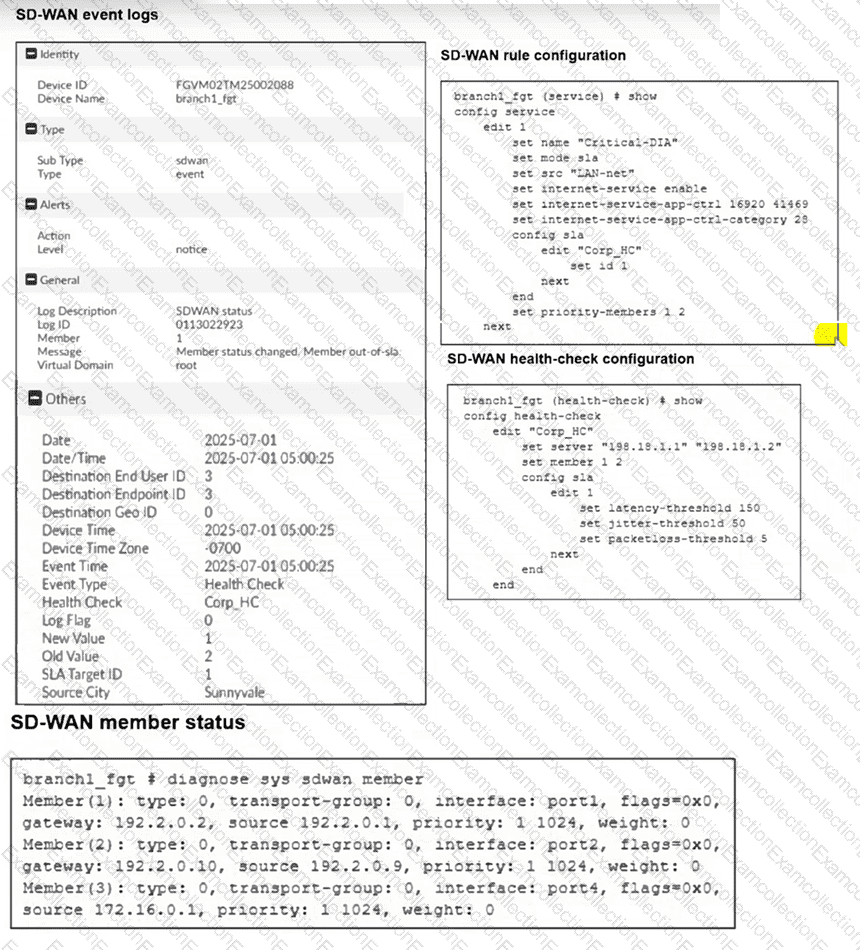
Two SD-WAN event logs, the member status, the SD-WAN rule configuration, and the health-check configuration for a FortiGate device are shown.
Immediately after the log messages are displayed, how will the FortiGate steer the traffic based on the information shown in the exhibits? Choose one answer.)
Exhibit.
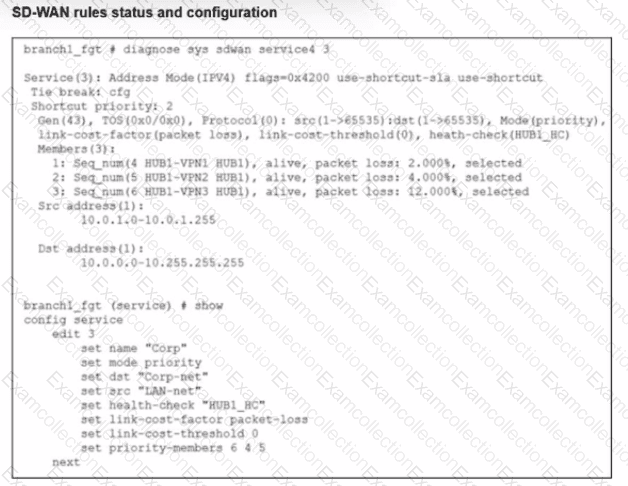
Refer to the exhibit, which shows the SD-WAN rule status and configuration.
Based on the exhibit, which change in the measured packet loss will make HUB1-VPN3 the new preferred member?
Refer to the exhibit.
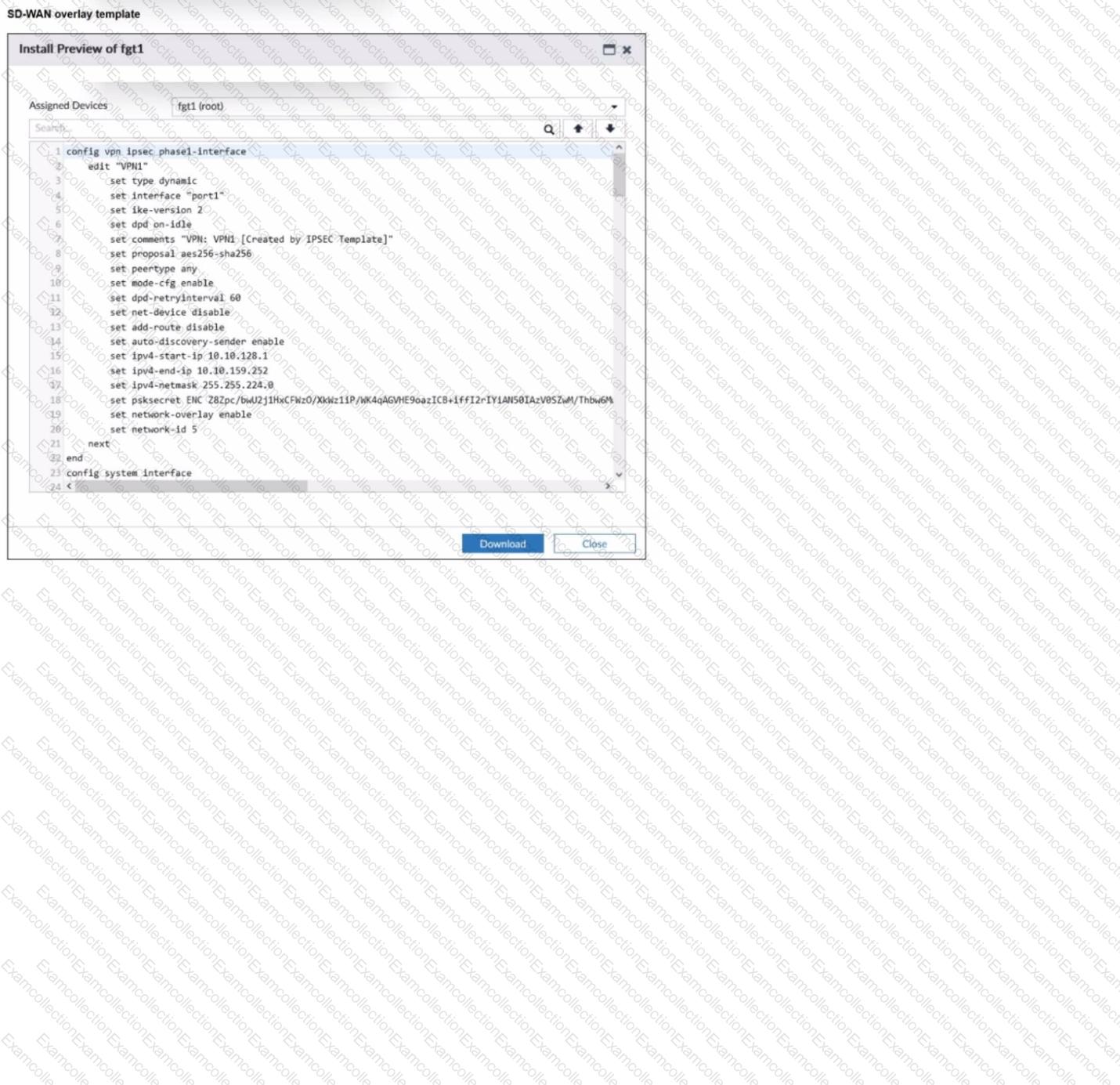
The administrator used the SD-WAN overlay template to prepare an IPsec tunnels configuration for a hub-and-spoke SD-WAN topology. The exhibit shows the FortiManager installation preview for one FortiGate device.
Based on the exhibit, which statement best describes the configuration applied to the FortiGate device?
Refer to the exhibits.

You connect to a device behind a branch FortiGate device and initiate a ping test. The device is part of the LAN subnet and its IP address is 10.0.1.101.
Based on the exhibits, which interface uses branch 1_fgt to steer the test traffic?
(You configure the overlay tunnels for an SD-WAN hub-and-spoke topology defined with IPsec tunnels, BGP on loopback, and dynamic BGP.
Which are two recommended IPsec settings for this topology? Choose two answers.)



