Fortinet NSE7_OTS-7.2 - Fortinet NSE 7 - OT Security 7.2
What can be assigned using network access control policies?
Which three common breach points can be found in a typical OT environment? (Choose three.)
Refer to the exhibit.
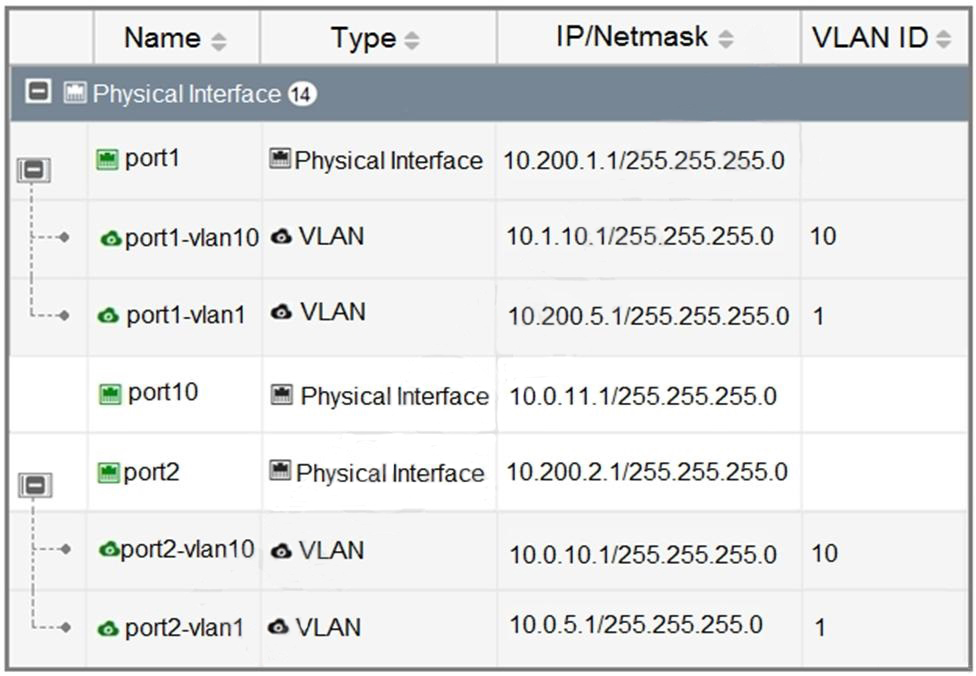
Which statement about the interfaces shown in the exhibit is true?
The OT network analyst runs different level of reports to quickly explore threats that exploit the network. Such reports can be run on all routers, switches, and firewalls. Which FortiSIEM reporting method helps to identify these type of exploits of image firmware files?
Refer to the exhibit.
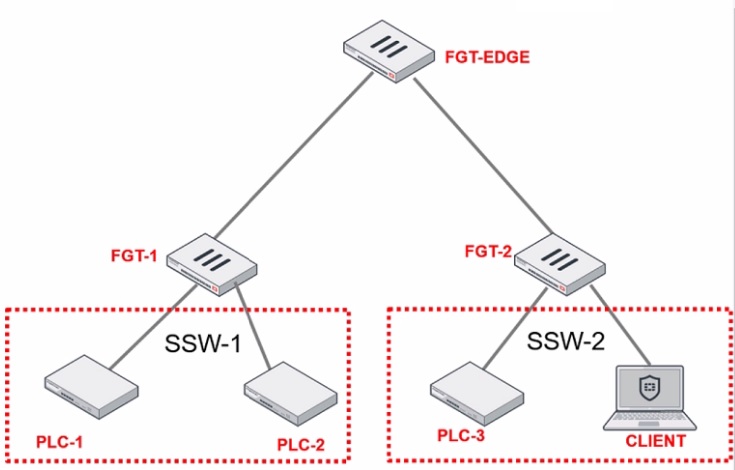
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT cannot send traffic to each other.
Which two statements about the traffic between PCL-1 and PLC-2 are true? (Choose two.)
An OT network administrator is trying to implement active authentication.
Which two methods should the administrator use to achieve this? (Choose two.)
As an OT network administrator you are required to generate reports that primarily use the same type of data sent to FortiSlEM These reports are based on the preloaded analytic searches
Which two actions can you take on FortiSlEM to enhance running reports for future use? (Choose two.)
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules?
Refer to the exhibit.
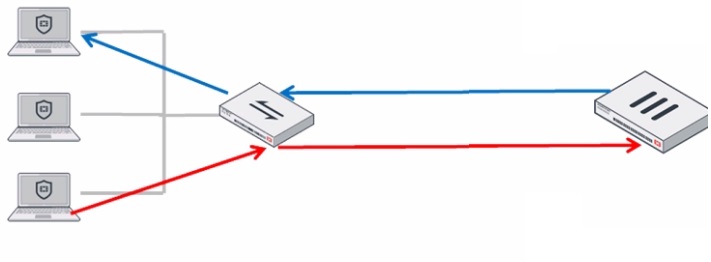
In order for a FortiGate device to act as router on a stick, what configuration must an OT network architect implement on FortiGate to achieve inter-VLAN routing?
Refer to the exhibit and analyze the output.
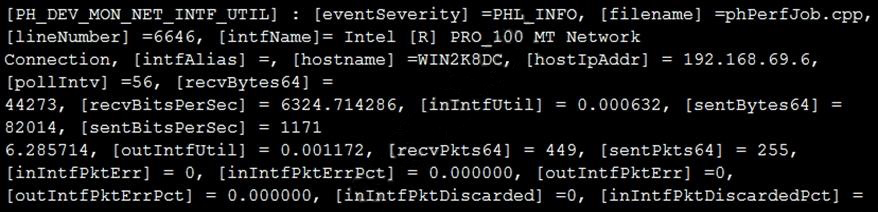
Which statement about the output is true?



