Fortinet NSE7_OTS-7.2 - Fortinet NSE 7 - OT Security 7.2
Which three Fortinet products can be used for device identification in an OT industrial control system (ICS)? (Choose three.)
As an OT network administrator you are managing three FortiGate devices that each protect different levels on the Purdue model To increase traffic visibility you are required to implement additional security measures to detect protocols from PLCs
Which security sensor must you implement to detect protocols on the OT network?
in an operation technology (OT) network FortiAnalyzer is used to receive and process logs from responsible FortiGate devices
Which statement about why FortiAnalyzer is receiving and processing multiple tog messages from a given programmable logic controller (PLC) or remote terminal unit (RTU) is true'?
An OT network architect needs to secure control area zones with a single network access policy to provision devices to any number of different networks.
On which device can this be accomplished?
Refer to the exhibit.
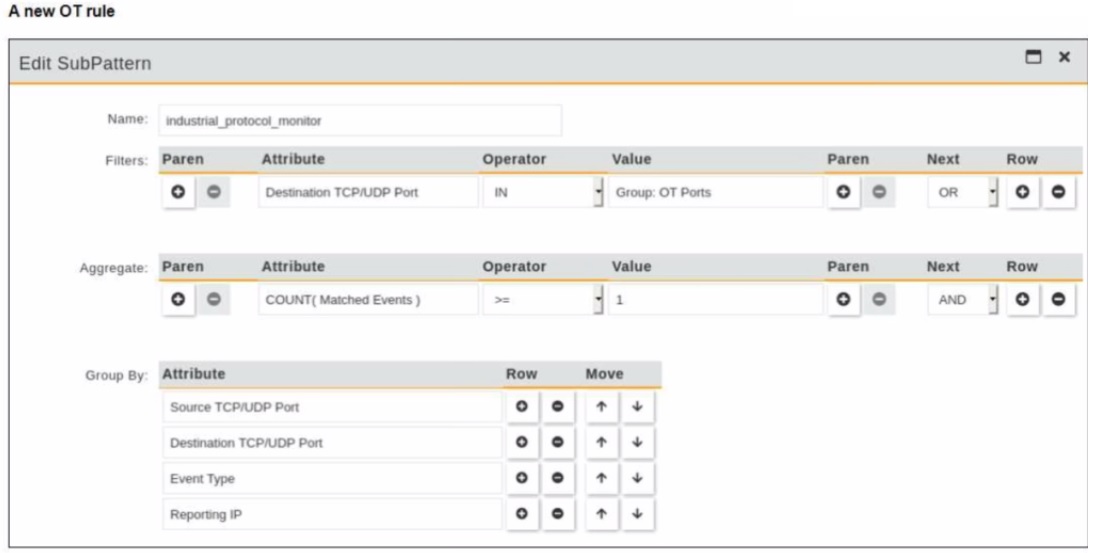
You are creating a new operational technology (OT) rule to monitor Modbus protocol traffic on FortiSIEM
Which action must you take to ensure that all Modbus messages on the network match the rule?
Refer to the exhibit.
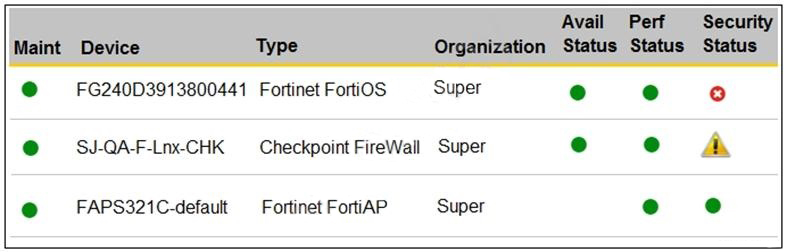
You are navigating through FortiSIEM in an OT network.
How do you view information presented in the exhibit and what does the FortiGate device security status tell you?
Refer to the exhibit.
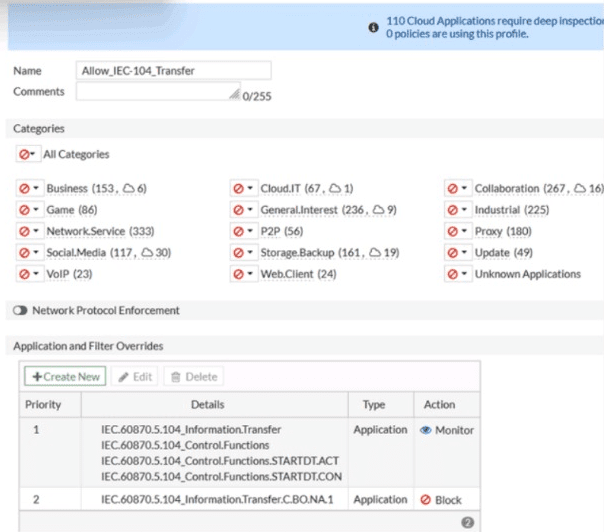
An OT network security audit concluded that the application sensor requires changes to ensure the correct security action is committed against the overrides filters.
Which change must the OT network administrator make?
An OT administrator deployed many devices to secure the OT network. However, the SOC team is reporting that there are too many alerts, and that many of the alerts are false positive. The OT administrator would like to find a solution that eliminates repetitive tasks, improves efficiency, saves time, and saves resources.
Which products should the administrator deploy to address these issues and automate most of the manual tasks done by the SOC team?
Which three common breach points can you find in a typical OT environment? (Choose three.)
Refer to the exhibit.
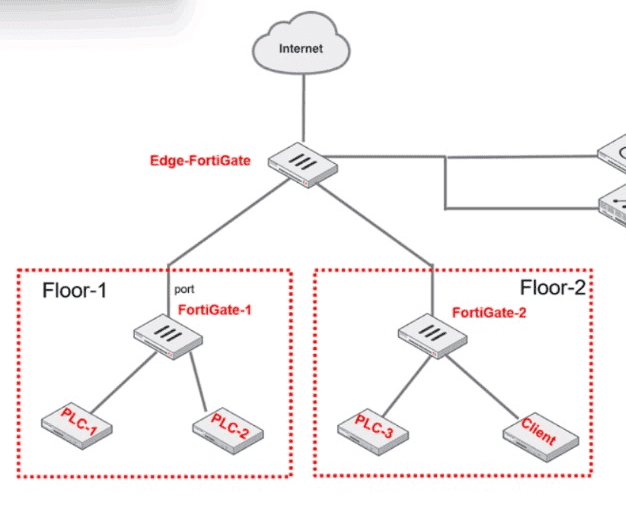
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the Layer 2 level.
What must the OT admin do to prevent Layer 2-level communication between PLC-3 and CLIENT?



