Fortinet NSE7_SOC_AR-7.6 - Fortinet NSE 7 - Security Operations 7.6 Architect
Refer to the exhibit.
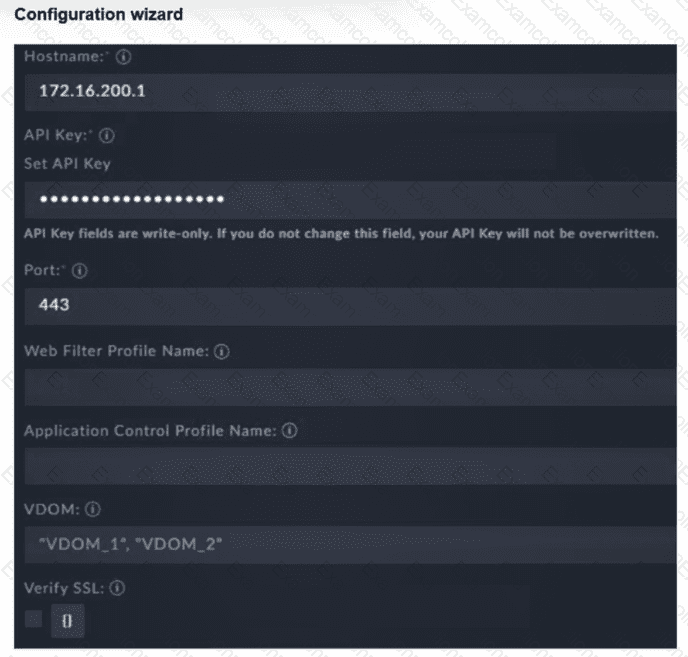
You must configure the FortiGate connector to allow FortiSOAR to perform actions on a firewall. However, the connection fails. Which two configurations are required? (Choose two answers)
Review the incident report:
An attacker identified employee names, roles, and email patterns from public press releases, which were then used to craft tailored emails.
The emails were directed to recipients to review an attached agenda using a link hosted off the corporate domain.
Which two MITRE ATT&CK tactics best fit this report? (Choose two answers)
Which three end user logs does FortiAnalyzer use to identify possible IOC compromised hosts? (Choose three.)
Refer to the exhibit.
Which two options describe how the Update Asset and Identity Database playbook is configured? (Choose two.)
Refer to the exhibit.
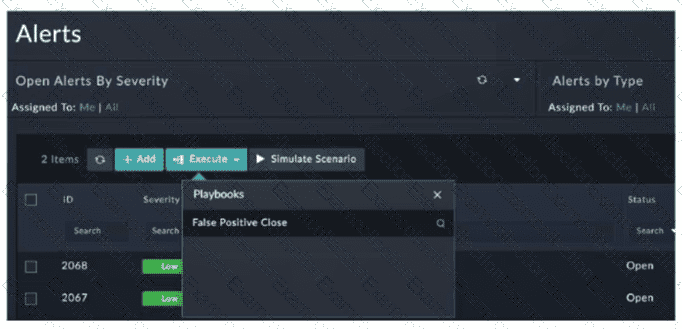
You configured a playbook namedFalse Positive Close, and want to run it to verify if it works. However, when you clickExecuteand search for the playbook, you do not see it listed. Which two reasons could be the cause of the problem? (Choose two answers)
Refer to the exhibits.
The FortiMail Sender Blocklist playbook is configured to take manual input and add those entries to the FortiMail abc. com domain-level block list. The playbook is configured to use a FortiMail connector and the ADD_SENDER_TO_BLOCKLIST action.
Why is the FortiMail Sender Blocklist playbook execution failing7
Which role does a threat hunter play within a SOC?



