Fortinet NSE7_SOC_AR-7.6 - Fortinet NSE 7 - Security Operations 7.6 Architect
Refer to the exhibit.
Assume that all devices in the FortiAnalyzer Fabric are shown in the image.
Which two statements about the FortiAnalyzer Fabric deployment are true? (Choose two.)
According to the National Institute of Standards and Technology (NIST) cybersecurity framework, incident handling activities can be divided into phases.
In which incident handling phase do you quarantine a compromised host in order to prevent an adversary from using it as a stepping stone to the next phase of an attack?
Which two ways can you create an incident on FortiAnalyzer? (Choose two answers)
Refer to the exhibits.
You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an event?
What are three capabilities of the built-in FortiSOAR Jinja editor? (Choose three answers)
Refer to Exhibit:
A SOC analyst is creating the Malicious File Detected playbook to run when FortiAnalyzer generates a malicious file event. The playbook must also update the incident with the malicious file event data.
What must the next task in this playbook be?
Refer to the exhibit.
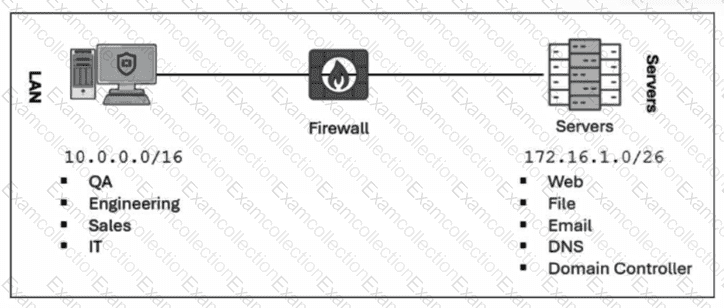
Which method most effectively reduces the attack surface of this organization? (Choose one answer)
Refer to the exhibits.

How is the investigation and remediation output generated on FortiSIEM? (Choose one answer)
When you use a manual trigger to save user input as a variable, what is the correct Jinja expression to reference the variable? (Choose one answer)
Review the incident report:
Packet captures show a host maintaining periodic TLS sessions that imitate normal HTTPS traffic but run on TCP 8443 to a single external host. An analyst flags the traffic as potential command-and-control. During the same period, the host issues frequent DNS queries with oversized TXT payloads to an attacker-controlled domain, transferring staged files.
Which two MITRE ATT&CK techniques best describe this activity? (Choose two answers)



