Pegasystems PEGACPRSA22V1 - Certified Pega Robotics System Architect 22
The variable varInput is a String that holds the value What is the output?
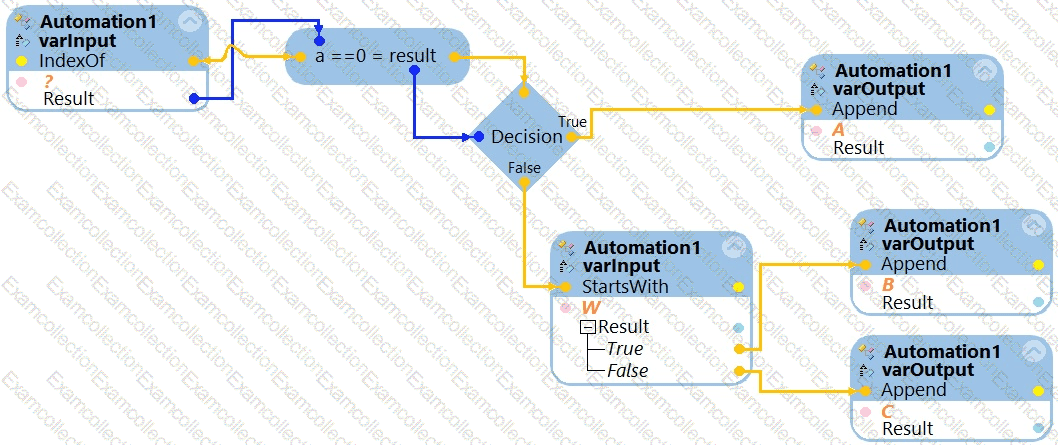
What is the outcome of the above automation?
You are assigned to develop a set of activities by using a popular HR application. The application loads automatically after you start interrogation from Pega Robot Studio, but you notice that you are unable to use the bullseye on the Robot Studio Interrogation Form to drag and drop over the desired controls.
Why are you unable to interrogate the desired application controls?
An automation requires the web adapter to attach to a running instance of Internet Explorer.
How do you achieve this requirement?
An application includes Assisted Sign-On by default with Pega Robot Studio?
Runtime produces an error when debugging a solution. The error message references that a control does not have the necessary value to complete an activity. The control depends upon the completion of a second activity in another project to provide its value.
Which two debugging options provide a benefit when referencing threads for issue resolution? (Choose two.)
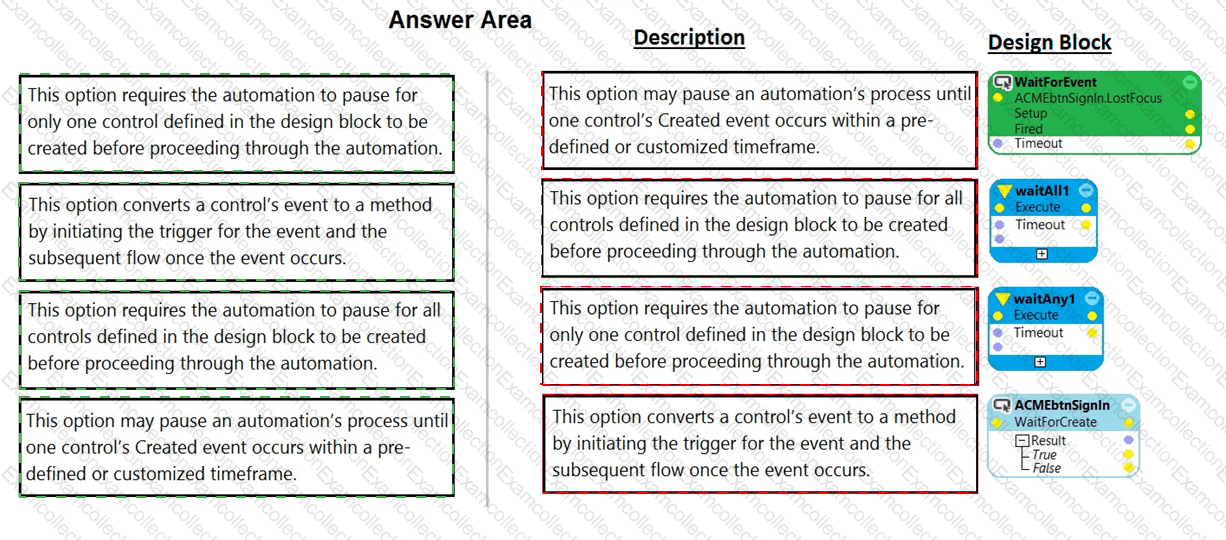
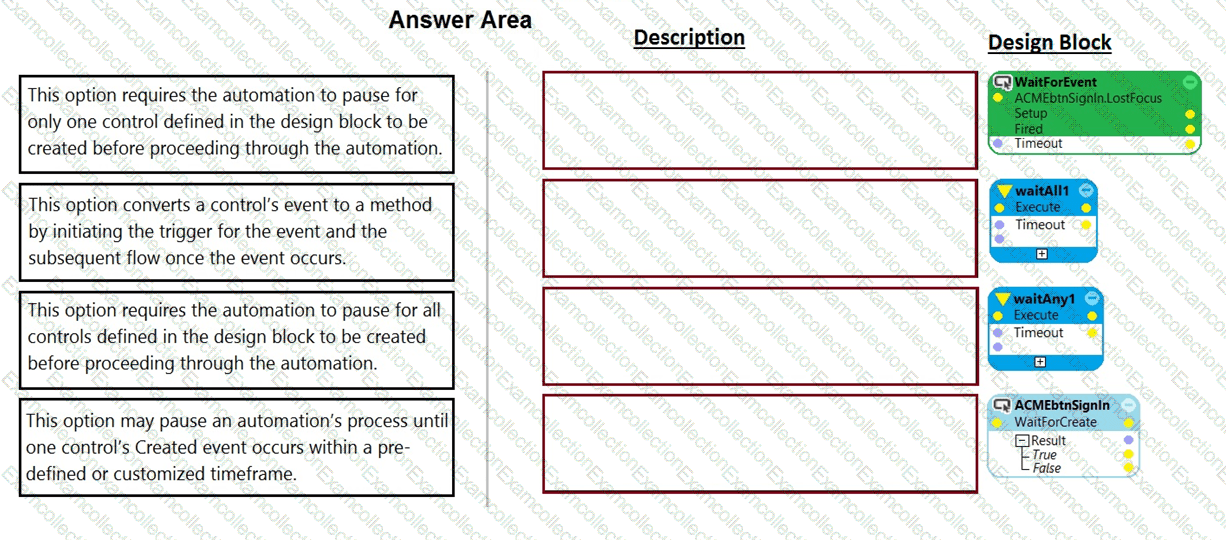
Pega Robot Studio has several methods to manage the flow of an automation depending on when a control is matched.
In the Answer Area, drag the description on the left to its matching Design Block.
Which three statements describe the characteristics of unattended automations? (Choose Three)
When developing automations and robotic projects for use with Pega applications, there are recommended design specifics and considerations for the developer. Of the options below, which three are recommended developer considerations? (Choose Three)
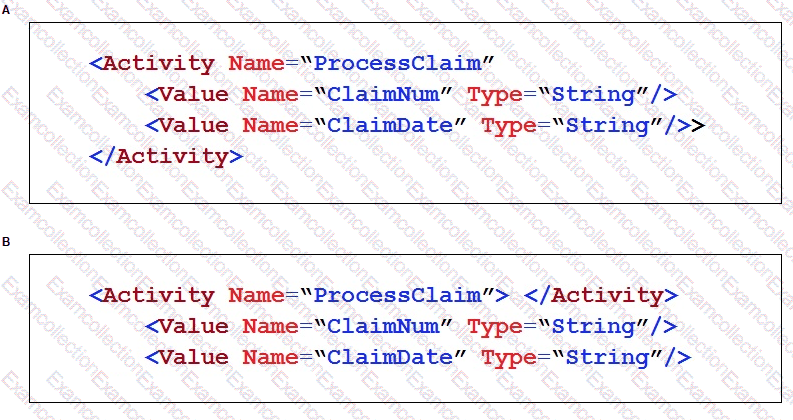
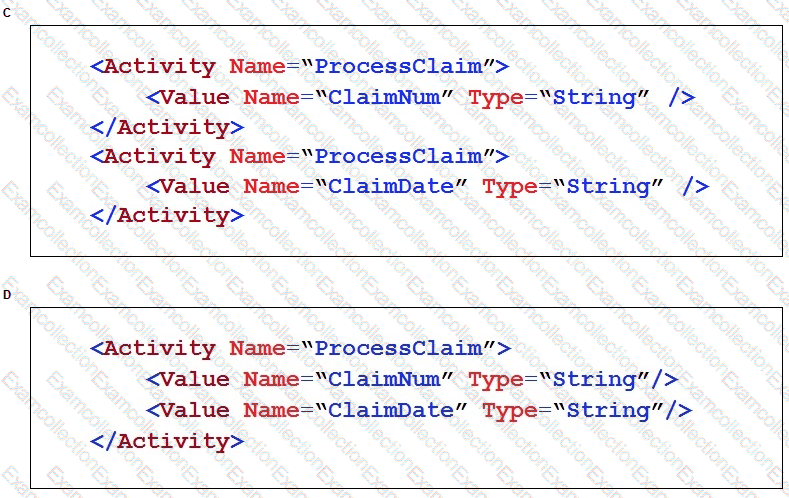
An Insurance Call Center project requires the use of the Interaction Framework. The supporting applications should perform specific work when processing claims. The claim requires the claim number and the claim date, but it may also share other claim information in the interaction’s context values.
Based on the information, which interaction.xml activity entry configures the project requirements?
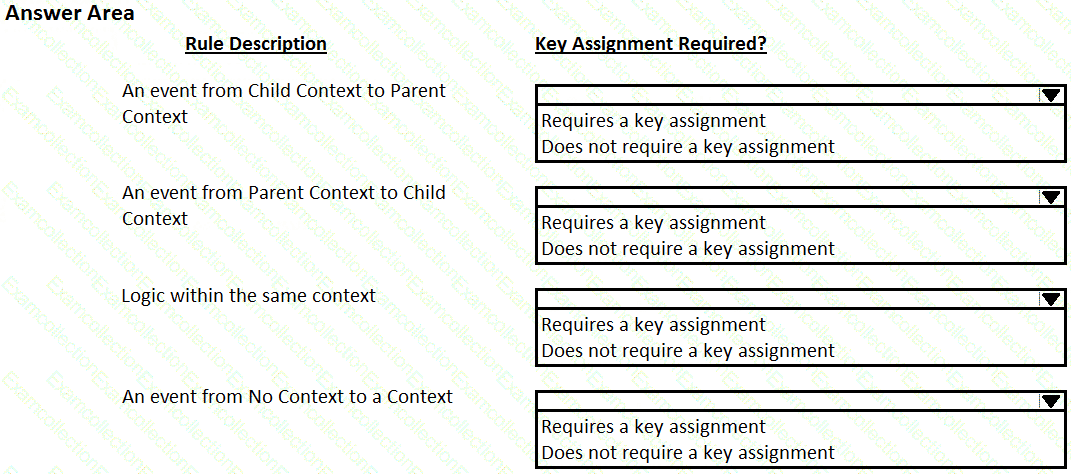
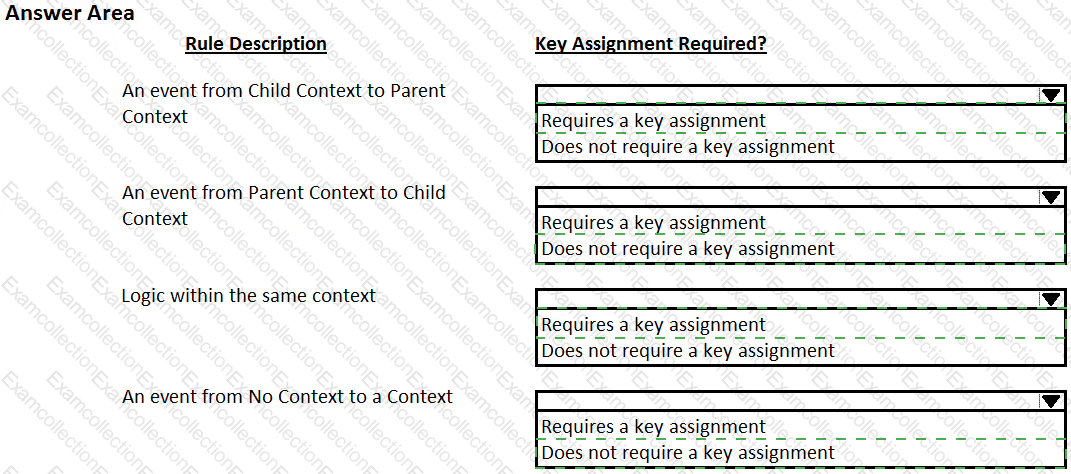
Pega Robot Studio provides five rules on how to differentiate between cloneable application objects when using key assignments in automations. The first rule states that an event creates the instance to set the context of a cloneable object. The remaining four rules state the requirements for a key assignment.
In the Answer Area, determine if each rule description requires a key assignment.