Microsoft SC-100 - Microsoft Cybersecurity Architect
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud.
You receive the following recommendations in Defender for Cloud
• Access to storage accounts with firewall and virtual network configurations should be restricted,
• Storage accounts should restrict network access using virtual network rules.
• Storage account should use a private link connection.
• Storage account public access should be disallowed.
You need to recommend a service to mitigate identified risks that relate to the recommendations. What should you recommend?
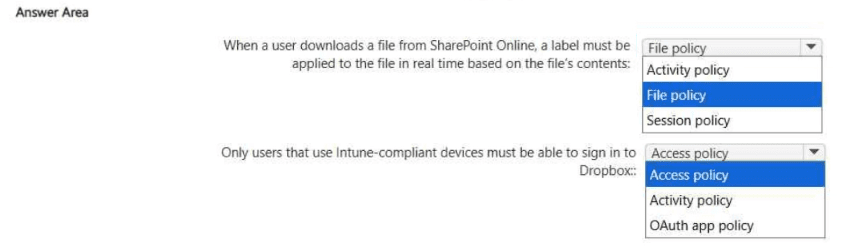
You have a Microsoft 365 E5 subscription. The subscription contains 1,000 devices that run Windows 11 Pro and are enrolled in Microsoft Intune. You need to recommend a Microsoft Defender for Cloud Apps solution that meets the following requirements:
• When a user downloads a file from Microsoft SharePoint Online, a label must be applied to the file in real time based on the file's contents.
• Only users that use Intune-compliant devices must be able to sign in to Dropbox.
Which type of policy should you recommend for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a security methodology for a DevOps development process based on the Microsoft Cloud Adoption Framework for Azure.
During which stage of a continuous integration and continuous deployment (CI/CD) DevOps process should each security-related task be performed? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point

You have an Azure AD tenant that syncs with an Active Directory Domain Services (AD DS) domain.
You are designing an Azure DevOps solution to deploy applications to an Azure subscription by using continuous integration and continuous deployment (CI/CD) pipelines.
You need to recommend which types of identities to use for the deployment credentials of the service connection. The solution must follow DevSecOps best practices from the Microsoft Cloud Adoption Framework for Azure.
What should you recommend?
Your company is designing an application architecture for Azure App Service Environment (ASE) web apps as shown in the exhibit. (Click the Exhibit tab.)
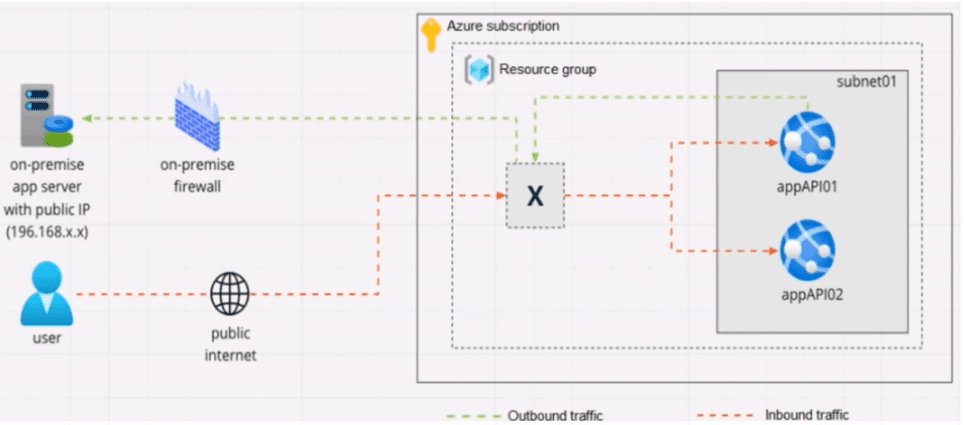
Communication between the on-premises network and Azure uses an ExpressRoute connection.
You need to recommend a solution to ensure that the web apps can communicate with the on-premises application server. The solution must minimize the number of public IP addresses that are allowed to access the on-premises network.
What should you include in the recommendation?
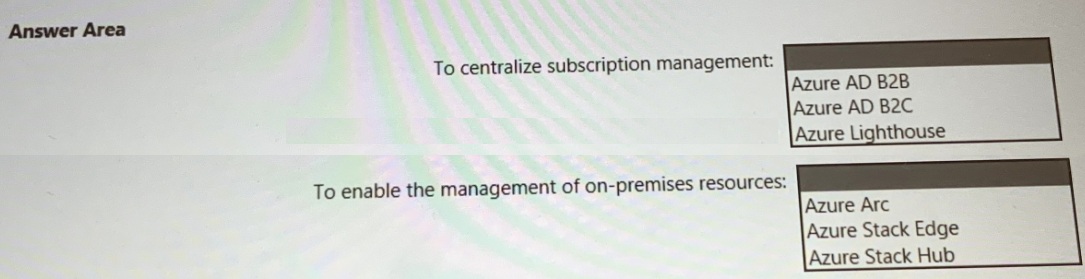
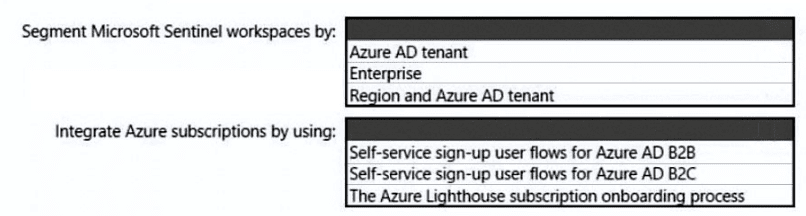
You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
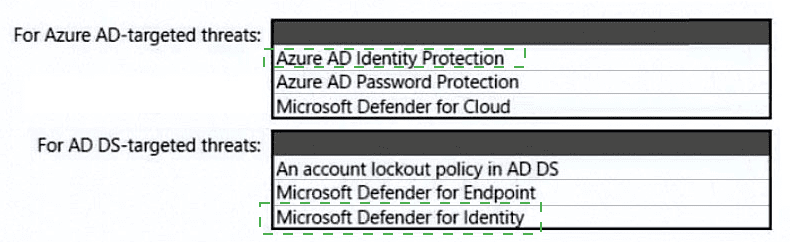
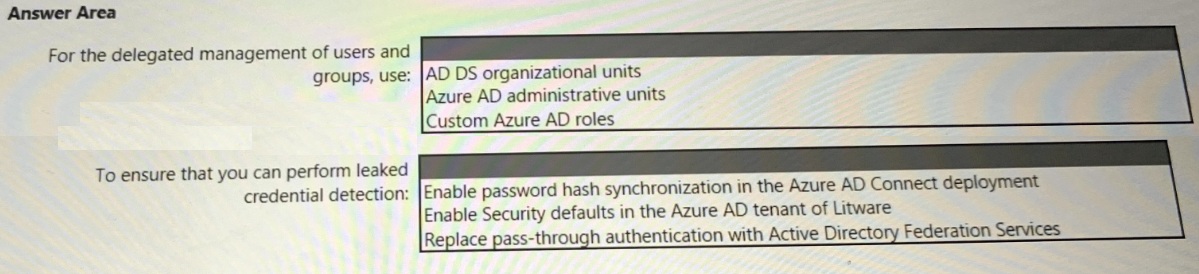
You need to recommend an identity security solution for the Azure AD tenant of Litware. The solution must meet the identity requirements and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements.
Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE; Each correct selection is worth one point.
You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements.
What should you configure for each landing zone?