CyberArk SECRET-SEN - CyberArk Sentry Secrets Manager
While retrieving a secret through REST, the secret retrieval fails to find a matching secret. You know the secret onboarding process was completed, the secret is in the expected safe with the expected object name, and the CCP is able to provide secrets to other applications.
What is the most likely cause for this issue?
You are setting up a Kubernetes integration with Conjur. With performance as the key deciding factor, namespace and service account will be used as identity characteristics.
Which authentication method should you choose?
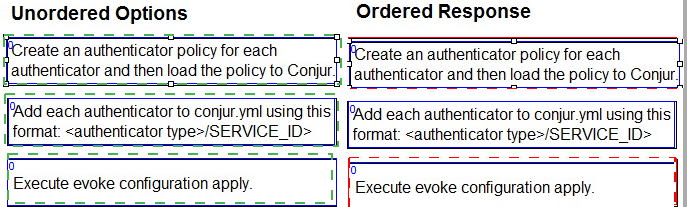
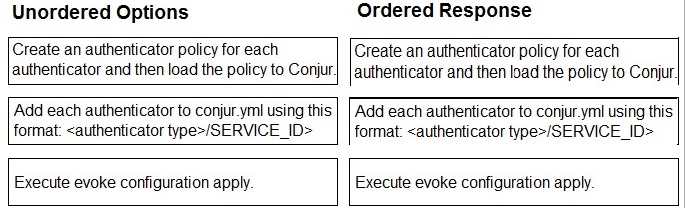
Arrange the steps to configure authenticators in the correct the sequence.
What is a main advantage of using dual accounts in password management?
While installing the first CP in an environment, errors that occurred when the environment was created are displayed; however, the installation procedure continued and finished successfully.
What should you do?
When using the Seed Fetcher to deploy Kubernetes Followers, an error occurs in the Seed Fetcher container. You check the logs and discover that although the Seed Fetcher was able to authenticate, it shows a 500 error in the log and does not successfully retrieve a seed file. What is the cause?
What is the most maintenance-free way to ensure a Conjur host’s access reflects any changes made to accounts in a safe in the CyberArk vault?
You modified a Conjur host policy to change its annotations for authentication.
How should you load the policy to make those changes?