Salesforce Salesforce-MuleSoft-Developer-II - Salesforce Certified MuleSoft Developer II (Mule-Dev-301)
Total 60 questions
A developer has created the first version of an API designed for business partners to work commodity prices.
What should developer do to allow more than one major version ofthe same API to be exposed by the implementation?
Refer to the exhibit.
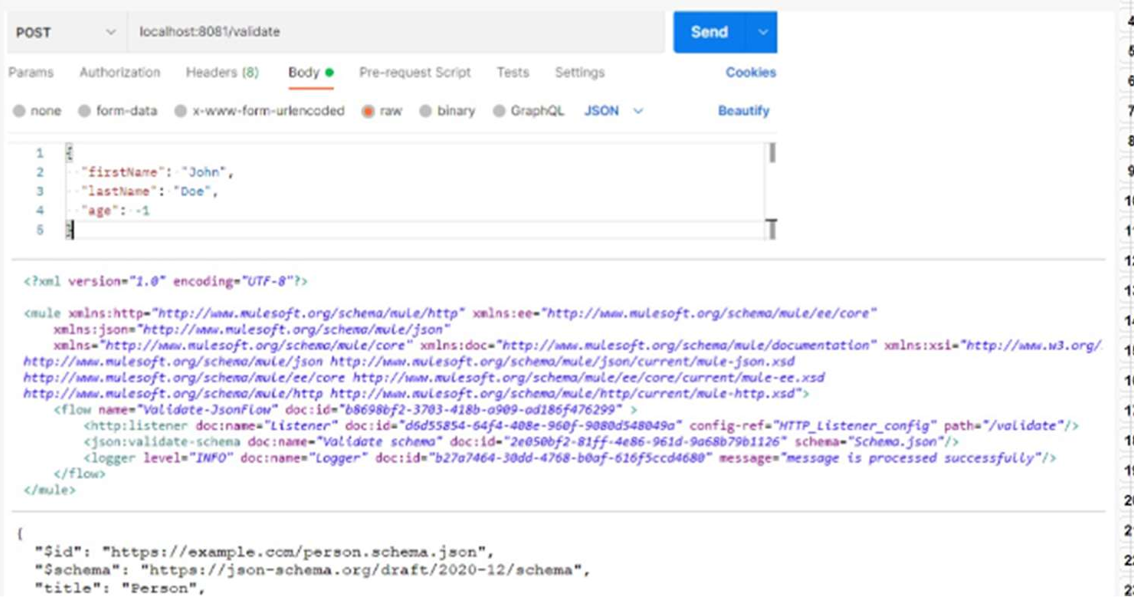
Based on the code snippet, schema,json file, and payload below, what is the outcome of the given code snippet when a request is sent with the payload?
Which pattern should be used to invoke multiple HTTP APIs in parallel and roll back failed requests in sequence?
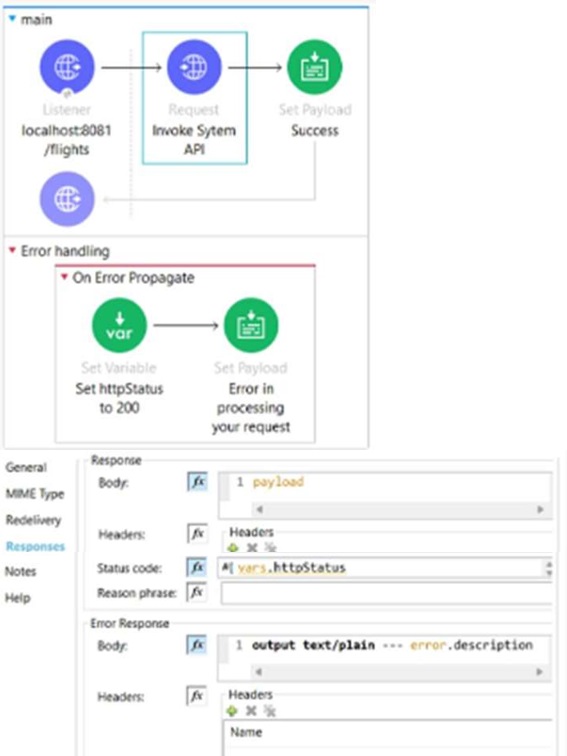
The HTTP Request operation raises an HTTP CONNECTIVITY error.
Which HTTP status code and body arereturned to the web client?
A Mule application need to invoice an API hosted by an externalsystem to initiate a process. The external API takes anywhere between one minute and 24 hours to compute its process.
Which implementation should be used to get response data from the external API after it completes processing?
An order processing system is composed of multiple Mule application responsible for warehouse, sales and shipping. Each application communication using Anypoint MQ. Each message must be correlated against the original order ID for observabilityand tracing.
How should a developer propagate the order ID as the correlation ID across each message?
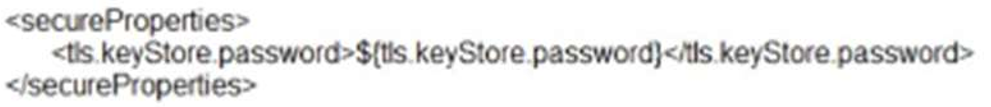
Refer to the exhibit.
What is the result of the Mule Maven Plugin configuration of the value of propertyits,keystorePassoword in CloudHub 2.0?
What is the MuleSoft recommended method to encrypt sensitive property data?



