Salesforce Salesforce-MuleSoft-Developer-II - Salesforce Certified MuleSoft Developer II (Mule-Dev-301)
Total 60 questions
A developer is working on a project that requires encrypting all data before sending it to a backend application. To accomplish this, the developer will use PGP encryption in the Mule 4 Cryptography module.
What is required to encrypt the data before sending it to the backend application?
A company has been using CI/CD. Its developers use Maven to handle build and deployment activities.
What is the correct sequence of activities that takes place during the Maven build and deployment?
A Mule implementation uses a HTTP Request within an Unit Successful scope to connect to an API.
How should a permanent error response like HTTP:UNAUTHORIZED be handle inside Until Successful to reduce latency?
Which pattern can a web API use to notify its client of state changes as soon as they occur?
Refer to the exhibit.
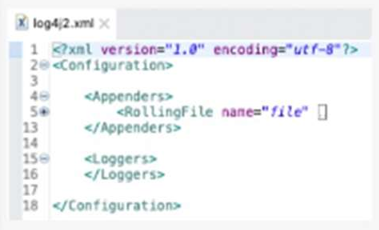
What action must be performed to log all the errors raised by the VM Connector?
Which type of cache invalidation does the Cache scope support without having to write any additional code?
A Mule application deployed to multiple Cloudhub 2.0 replicas needs to temporarily persist large files over 10MB between flow executions, and routinely needs to query whether the file data exists on separate executions.
How can this be achieved?
Two APIs are deployed to a two-node on-prem cluster. Due to a requirements change, the two APIs must communicate to exchange data asynchronously.
Which configurations are required for HTTP Listener to enable mTLS authentication?
Refer to the exhibits.
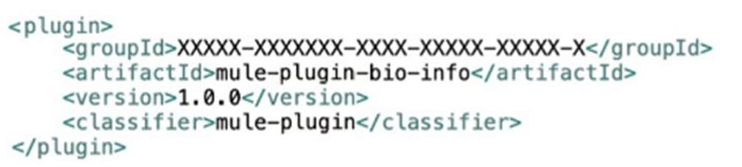
Bioinfo System API is implemented and published to Anypoint Exchange. Adeveloper wants to invoke this API using its REST Connector.
What should be added to the POM?
A)
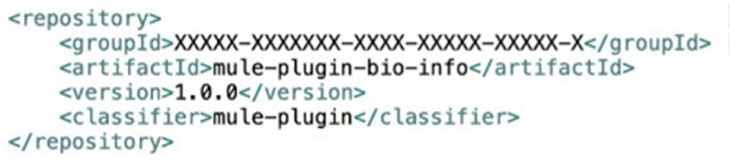
B)
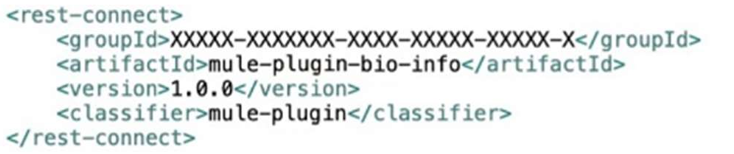
C)
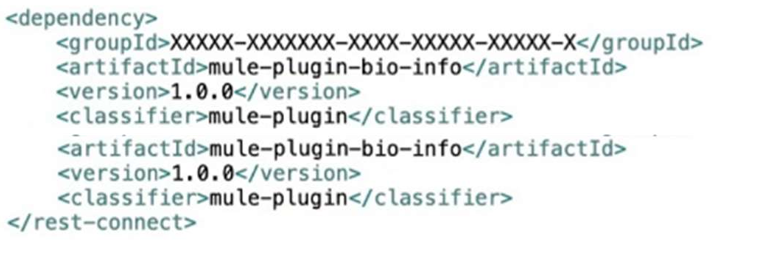
D)
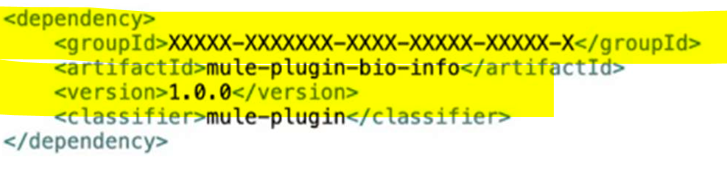
E)