Microsoft MS-102 - Microsoft 365 Administrator Exam
Which role should you assign to User1?
Available Choices (select all choices that are correct)
: 221
You have a Microsoft 365 E5 subscription.
Users have the devices shown in the following table.
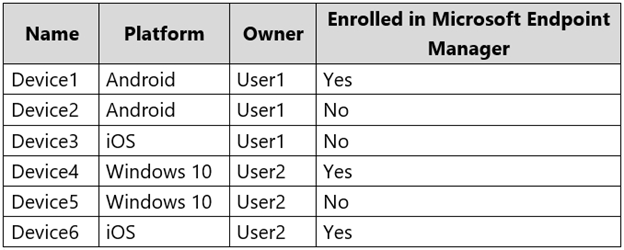
On which devices can you manage apps by using app configuration policies in Microsoft Endpoint Manager?
You are evaluating the required processes for Project1.
You need to recommend which DNS record must be created while adding a domain name for the project.
Which DNS record should you recommend?
You have a Microsoft 365 subscription.
You add a domain named contoso.com.
When you attempt to verify the domain, you are prompted to send a verification email to admin@contoso.com.
You need to change the email address used to verify the domain.
What should you do?
You have a Microsoft 365 E5 subscription that contains a user named User1.
User1 exceeds the default daily limit of allowed email messages and is on the Restricted entities list. You need to remove User1 from the Restricted entities list. What should you use?
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
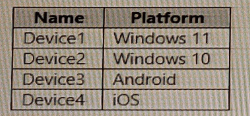
All the devices are onboarded To Microsoft Defender for Endpoint
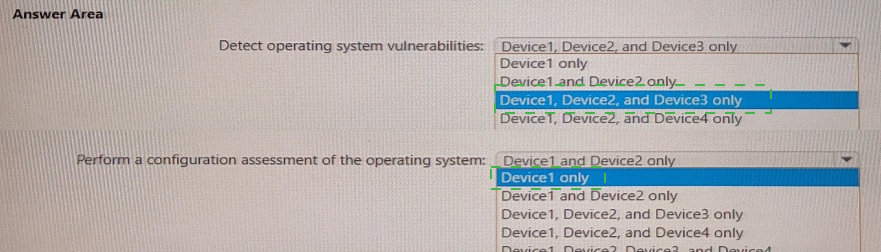
You plan to use Microsoft Defender Vulnerability Management to meet the following requirements:
• Detect operating system vulnerabilities.
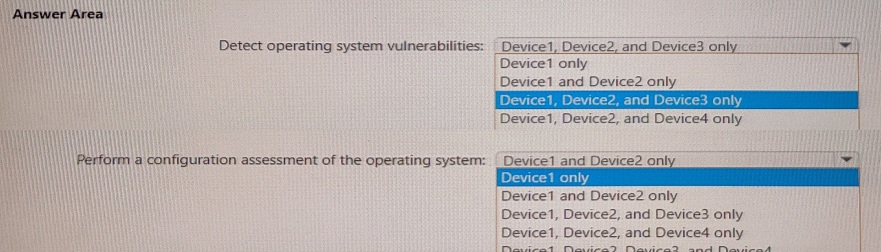
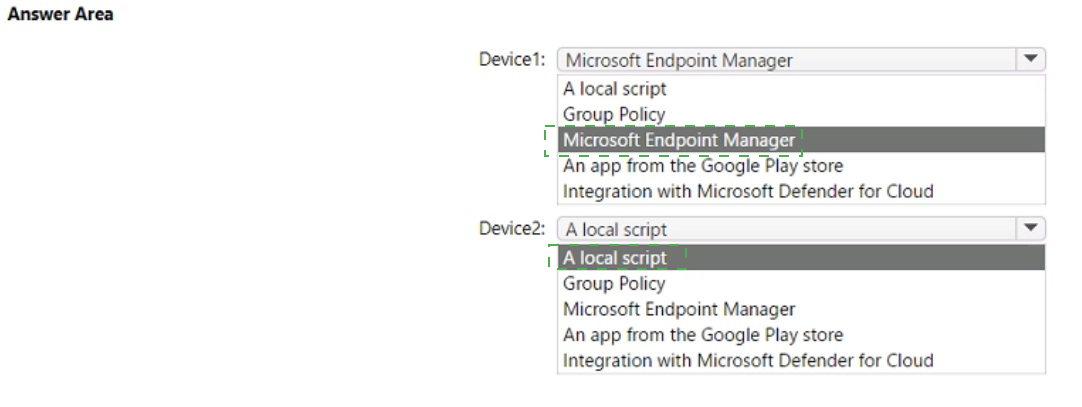
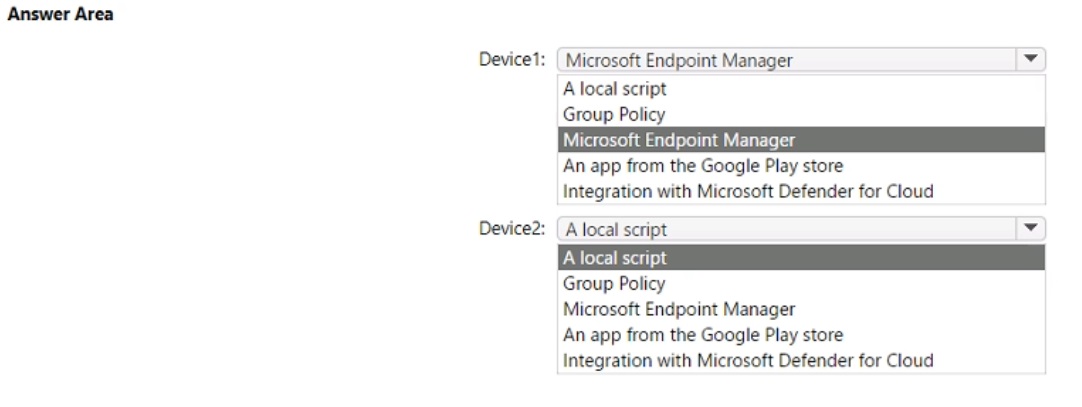
You have a Microsoft 365 E5 subscription that uses Microsoft Intune and contains the devices shown in the following table.
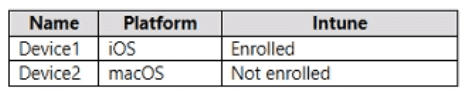
You need to onboard Device1 and Device2 to Microsoft Defender for Endpoint.
What should you use to onboard each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
: 249 HOTSPOT
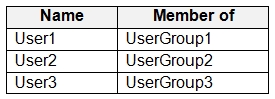
You have a Microsoft 365 E5 tenant that contains the users shown in the following table.
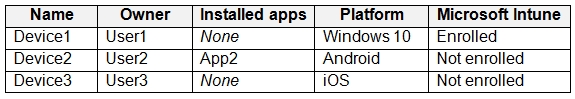
The tenant contains the devices shown in the following table.
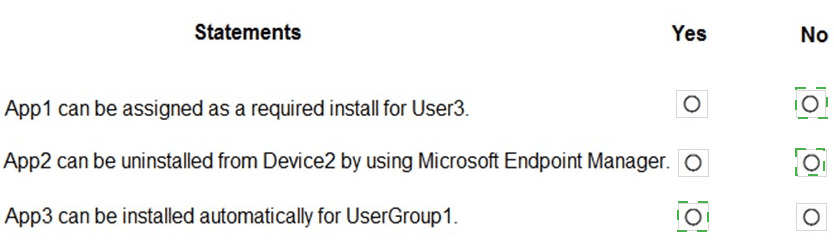
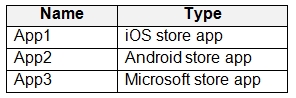
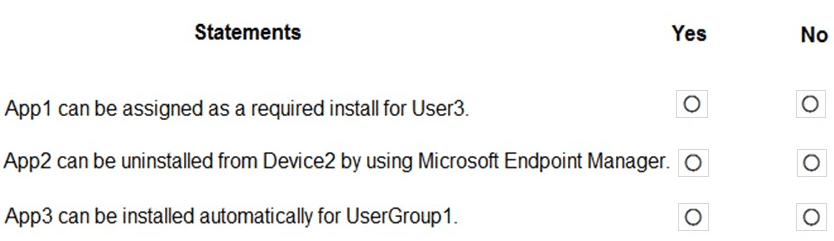
You have the apps shown in the following table.
You plan to use Microsoft Endpoint Manager to manage the apps for the users.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
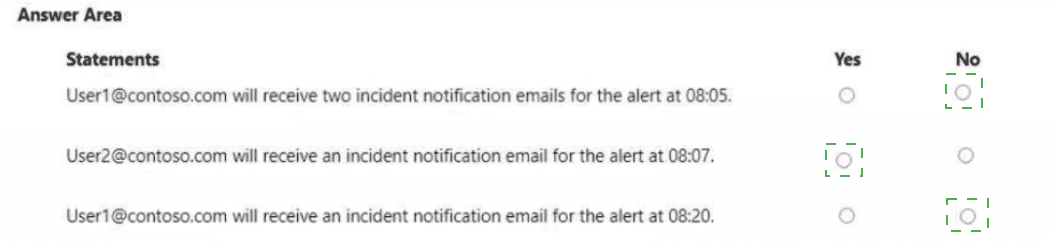
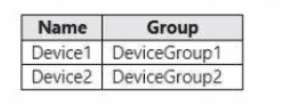
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
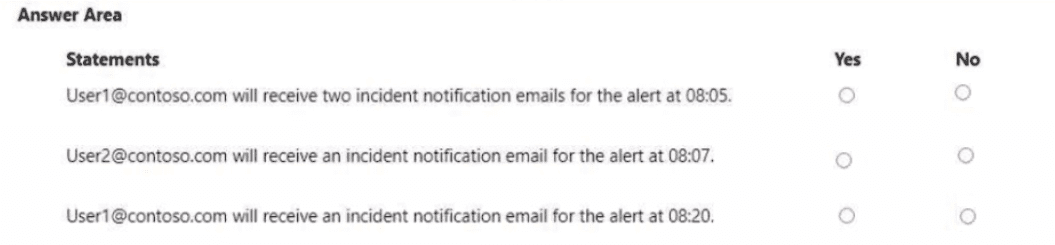
At 08:00. you create an incident notification rule that has the following configurations:
• Name: Notification!
• Notification settings
o Notify on alert seventy: Low
o Device group scope: All (3)
o Details: First notification per incident
• Recipients: Userl@contoso.com, User2@contoso.com
At 08:02. you create an incident notification rule that has the following configurations:
• Name: Notification
• Notification settings
o Notify on alert severity: Low. Medium
o Device group scope: DevtceGroup1, DeviceGroup2
• Recipients: Userl@contoso.com
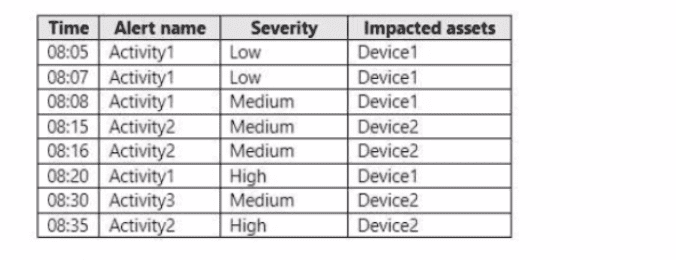
in Microsoft 365 Defender, alerts are logged as shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No1.
NOTE: Each correct selection is worth one point.
Note: This section contains one or more sets of questions with the same scenario and problem. Each question presents a unique solution to the problem. You must determine whether the solution meets the stated goals. More than one solution in the set might solve the problem. It is also possible that none of the solutions in the set solve the problem.
After you answer a question in this section, you will NOT be able to return. As a result, these questions do not appear on the Review Screen.
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Office 365.
You need to implement a threat policy that will apply a balanced baseline protection profile to protect against spam, phishing, and malware.
Solution: You create a Strict preset security policy.
Does this meet the goal?